Have you ever wondered if your email address and associated data have been compromised in a data breach? With the increasing number of online security breaches, it’s crucial to stay vigilant. Fortunately, several free online tools can help you quickly determine if your email address has been leaked and provide guidance on protecting your accounts. This article explores these tools and provides actionable steps to take if your email appears in a breach.
HaveIBeenPwned: A Comprehensive Breach Check
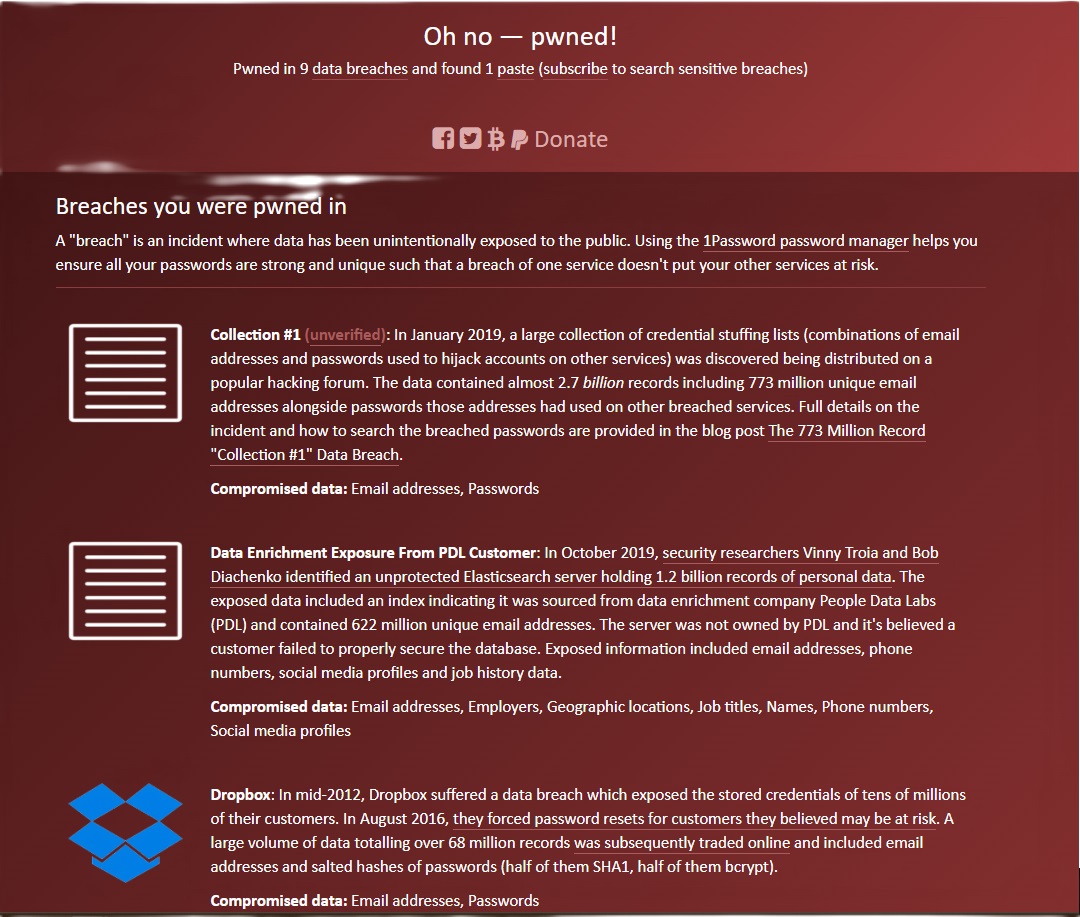
HaveIBeenPwned, created by security expert Troy Hunt, is a widely recognized service that allows you to check if your email address has been exposed in a data breach. Simply enter your email address on the website, and the tool will instantly reveal if it’s been compromised.
 haveibeenpwned
haveibeenpwned
The results will show the breaches where your email was found, along with recommendations on improving your account security. HaveIBeenPwned also details which breaches exposed your associated passwords. Additionally, the site offers phone number and password checks and an optional notification service that alerts you if your email appears in future breaches.
It’s important to note that even if your email isn’t found in a breach, it doesn’t guarantee complete security. A weak password can still make your account vulnerable. Conversely, an email appearing in a breach doesn’t necessarily mean it’s actively being misused. Troy Hunt also maintains a Twitter channel dedicated to data breaches, offering further insights and updates.
HPI Identity Leak Checker: Email-Based Results
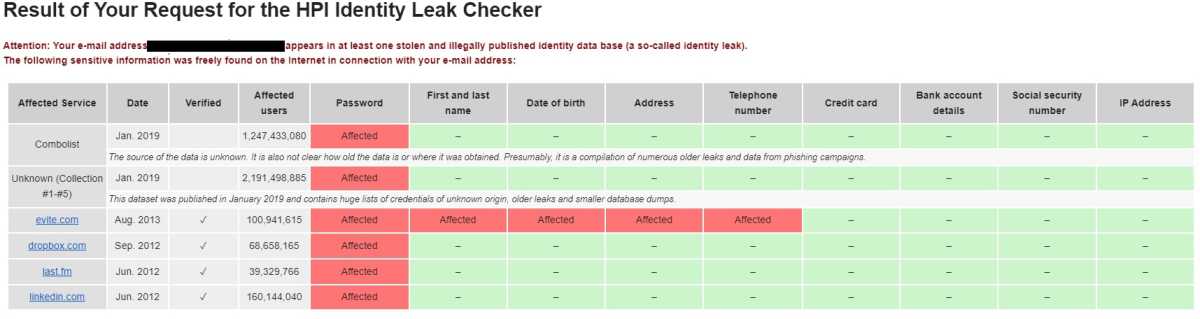
The Hasso Plattner Institute for Digital Engineering (HPI) offers another free tool, the HPI Identity Leak Checker. Unlike HaveIBeenPwned, this tool doesn’t display results directly on the website. Instead, it sends an email to the address you entered containing the analysis.
 HPI Identity Leak Checker
HPI Identity Leak Checker
This email-based approach prevents potential misuse for stalking, a theoretical concern with publicly displayed results. The HPI Identity Leak Checker focuses on whether your password was found in a leak, not whether it’s still active for the affected account. Consequently, even if you’ve changed your password, the tool may still issue a warning if your old password remains in the leaked data.
University of Bonn Identity Leak Checker: Another Privacy-Focused Option
Similar to the HPI tool, the University of Bonn’s Identity Leak Checker sends results via email, enhancing privacy. This tool was developed as part of the German government-subsidized EIDI project. By receiving results privately, users can avoid potential stalking or spying attempts.
Protecting Yourself After a Breach
If any of these tools reveal that your email address has been compromised, take immediate action:
- Change your password: Update the password for the affected email account and any other services using the same password.
- Enable Two-Factor Authentication (2FA): This crucial security measure adds an extra layer of protection to your accounts.
- Use a Password Manager: A password manager helps create and securely store strong, unique passwords for all your online accounts.
Understanding the Source of Leaked Data
Most leaked email addresses originate from attacks on company servers that store user data. These breaches can expose vast amounts of personal information, which is often sold on the darknet or in online forums. Examples of large-scale data breaches include the Comcast Xfinity hack, the Western Digital hack, and repeated breaches affecting LastPass.
While individuals are powerless to prevent these server-side breaches, taking proactive steps to secure your accounts can significantly mitigate the potential damage.
Conclusion: Stay Proactive and Protect Your Data
Checking your email address for breaches is a simple yet essential step in maintaining your online security. Utilize the free tools discussed in this article to monitor your online presence and take immediate action if your email is found in a compromised database. By following the recommended security practices, you can minimize the risks associated with data breaches and safeguard your valuable information.










