With the increasing frequency of data breaches, receiving notifications about compromised accounts has become commonplace. However, before clicking any links in these emails, exercise caution. That notification might be a phishing scam.
These deceptive emails aim to trick you into revealing sensitive information like login credentials or personal details. Phishing attacks vary in their approach. Some impersonate legitimate companies, while others masquerade as security software providers like Norton or Malwarebytes, which often send legitimate emails about online threats.
To avoid falling victim to these scams, refrain from clicking any links within the email. Instead, open a new browser tab and search for the company name along with “data breach” or “hacked.” Legitimate breaches are typically reported in the news or on the company’s official website. These sources will also provide verified information on securing your account.
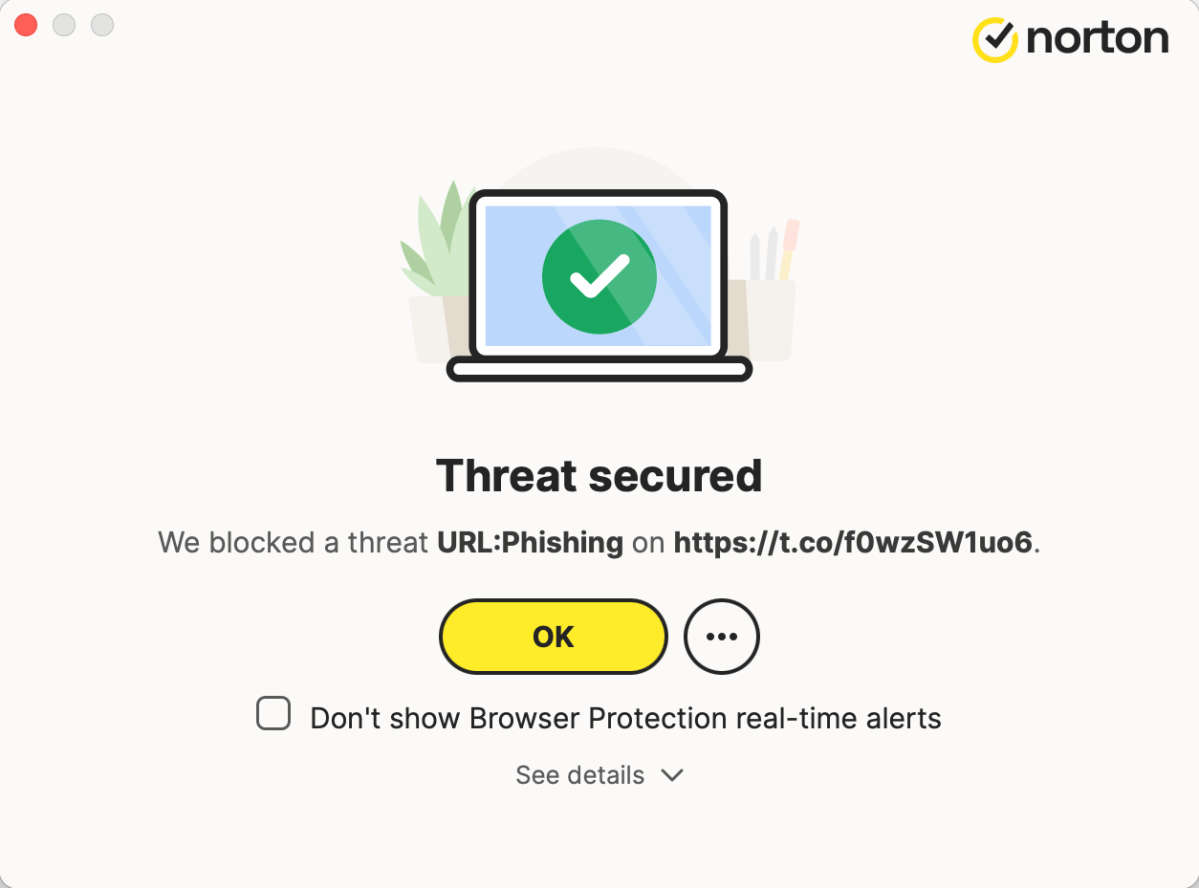 Antivirus software blocking a phishing threatAntivirus software acts as a crucial second line of defense against malicious links.
Antivirus software blocking a phishing threatAntivirus software acts as a crucial second line of defense against malicious links.
Furthermore, implement these strategies to protect yourself from phishing attempts:
-
Activate antivirus software: Windows Security provides default protection, but consider reputable third-party antivirus software for enhanced features. While not infallible, these applications can detect and block suspicious URLs, mitigating the risk of accidental clicks.
-
Update your browser: Modern browsers like Chrome and Firefox actively block known malicious links. Regular updates ensure you have the latest security patches.
-
Utilize passkeys: Phishing sites often target login information. Passkeys, designed for use only with the original site they’re created for, prevent your credentials from being compromised.
-
Employ virtual credit card numbers: These protect your financial data by limiting usage to a single merchant or a specific dollar amount, minimizing potential damage if stolen. They are also easily canceled.
Feeling overwhelmed by data breaches and online security concerns is understandable. Fortunately, most software maintenance is now automated. Once passkeys are set up, they eliminate the need for regular password changes. The key challenge lies in developing a habit of distrusting links in emails, a practice that becomes easier with consistent effort.