The internet we experience daily through browsers like Chrome, Firefox, and Safari is merely the tip of the iceberg. Beneath the surface lies the darknet, a hidden network offering anonymity and a haven for information exchange, as highlighted by PCWorld back in 2013. While valuable for freedom of information in censored regions, this anonymity also attracts criminal activity. The darknet’s marketplaces offer not only illicit goods like drugs and weapons but also stolen data such as credit card information and forged documents. This duality has brought the darknet under increasing public scrutiny, particularly due to its association with various criminal offenses.
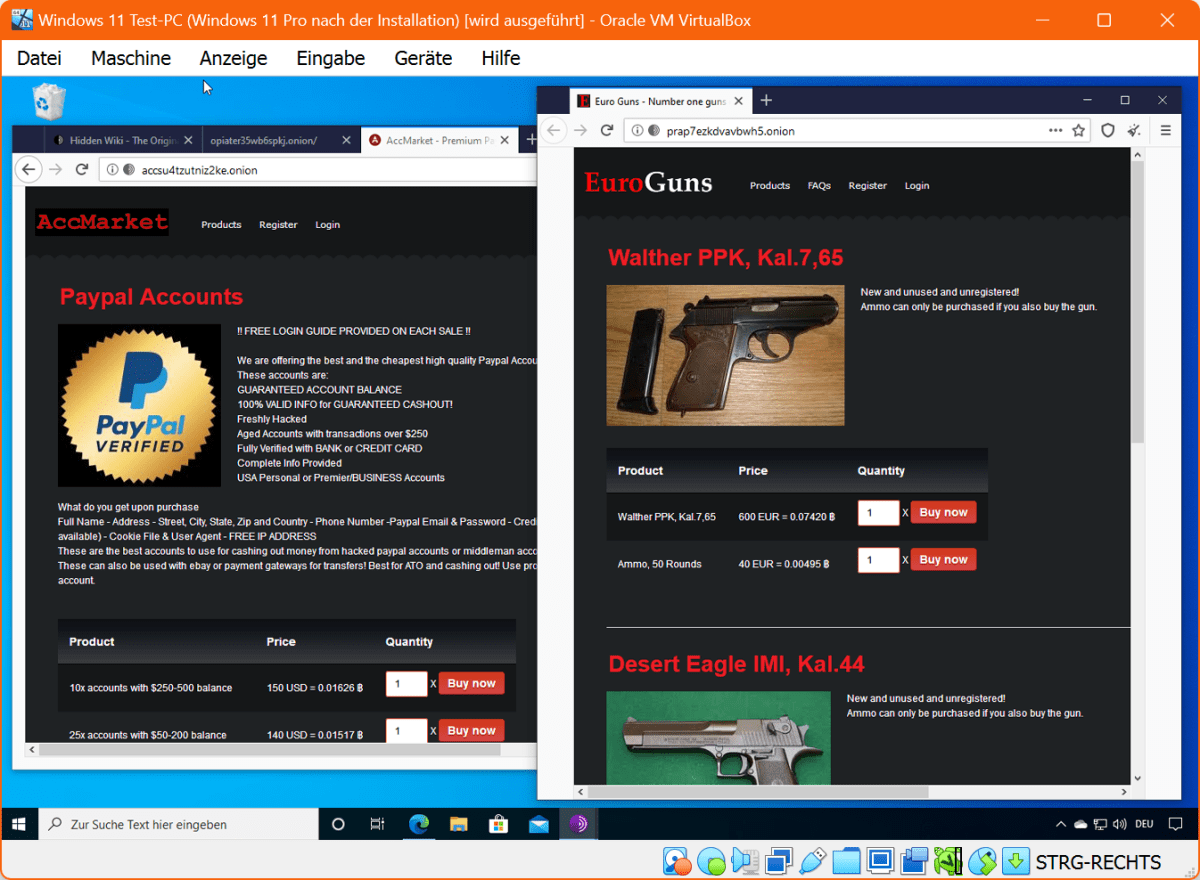 Hacked PayPal accounts, counterfeit money, drugs, weapons, and much more — the darknet is teeming with illegal offers. That’s why its users want to remain unrecognized at all costs.Darknet marketplaces offer a range of illicit goods and services, driving the need for user anonymity.
Hacked PayPal accounts, counterfeit money, drugs, weapons, and much more — the darknet is teeming with illegal offers. That’s why its users want to remain unrecognized at all costs.Darknet marketplaces offer a range of illicit goods and services, driving the need for user anonymity.
Understanding the Darknet
The term “darknet” reflects its primary purpose: enabling anonymous online communication. Anonymization services mask internet activity, preventing tracking and surveillance. However, this anonymity only holds true if users avoid revealing personal information, such as logging into social media or email accounts. The Tor network is a popular choice for anonymization. Beyond its cloaking capabilities, Tor also hosts hidden websites inaccessible through conventional browsers. These hidden sites reside on Tor servers and constitute a significant portion of the darknet.
Tor: The Gateway to the Darknet
Tor, short for “The Onion Router,” derives its name from its layered encryption method. To conceal a user’s location, the Tor software routes data packets through multiple randomly selected computers (nodes) before reaching the open internet via an exit node. Each node decrypts a single layer of encryption, like peeling an onion. This process ensures data remains unreadable to eavesdroppers on any intermediary node.
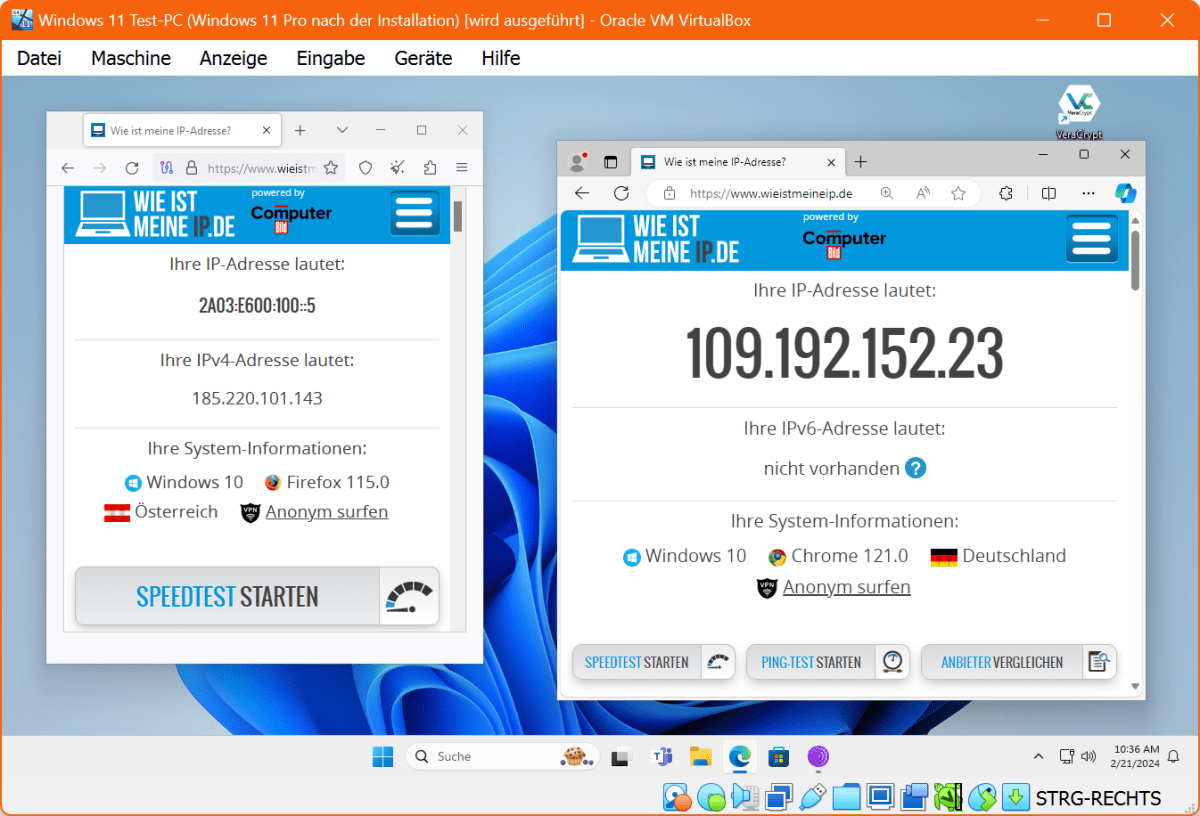 This is how darknet users surf anonymously: While the Tor browser (left window) displays a fictitious IP address, Microsoft Edge displays the real one. In a virtual machine, the browser leaves even fewer traces.Tor Browser masks a user’s true IP address, enhancing anonymity.
This is how darknet users surf anonymously: While the Tor browser (left window) displays a fictitious IP address, Microsoft Edge displays the real one. In a virtual machine, the browser leaves even fewer traces.Tor Browser masks a user’s true IP address, enhancing anonymity.
This layered encryption also facilitates the concealment of websites and web addresses. Hidden websites are hosted on servers within the Tor network, their addresses encrypted and only decipherable by specific Tor connection nodes. These encrypted addresses use the “.onion” domain extension and are often listed on directories like the community-edited Hidden Wiki and search engines like Torch, Ahmia, and Haystack.
When a user clicks a “.onion” link, the request travels through multiple nodes but bypasses the exit node. Instead, it reaches a connection node that knows the hidden server’s true address. This node retrieves the data and forwards it to the user, effectively masking the server’s location. This architecture renders traditional methods of locating servers ineffective and also makes using file-sharing services like BitTorrent over Tor impractical.
Navigating the Darknet
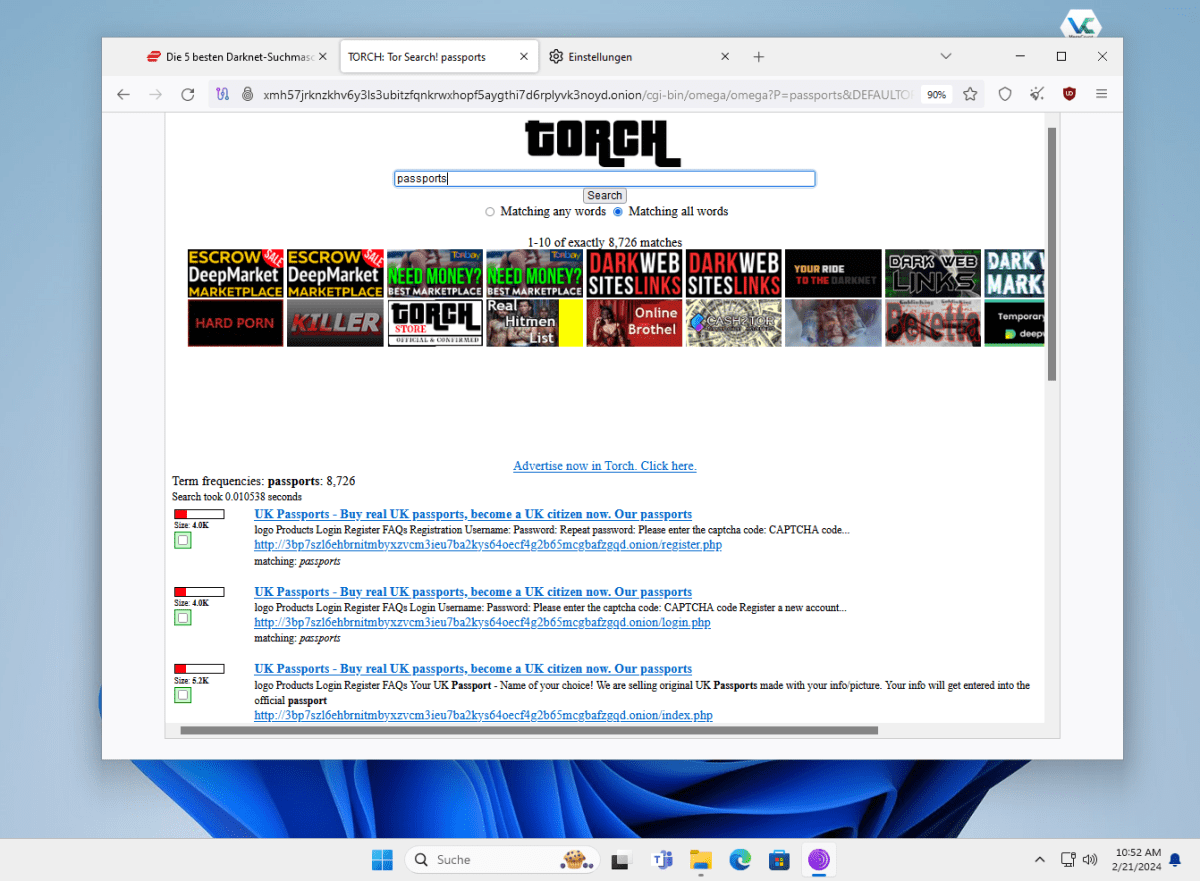 You cannot simply carry out a normal Google search on the darknet. You need a darknet search engine like Torch, Ahmia, and Haystack, or a directory like the Hidden Wiki.Specialized search engines and directories are essential for navigating the darknet.
You cannot simply carry out a normal Google search on the darknet. You need a darknet search engine like Torch, Ahmia, and Haystack, or a directory like the Hidden Wiki.Specialized search engines and directories are essential for navigating the darknet.
Exploring the darknet through directories like the Hidden Wiki reveals a vast array of illicit offerings, from stolen financial data to drugs and weapons. Transactions typically utilize Bitcoin for its anonymity and untraceable nature.
Enhancing Anonymity with Virtual Machines
Many darknet users employ the Tor browser within a virtual machine to further minimize their digital footprint. While the Tor Browser itself is not illegal and can be used for legitimate anonymous browsing, running it within a virtual machine adds an extra layer of separation between the user’s activities and their primary operating system.
To connect, simply click “Connect” in the Tor Browser. The “Configure” option is relevant only for users needing to connect via a proxy server or bypass censorship in countries where Tor is blocked. Verifying Tor’s functionality is simple: compare your IP address displayed on a site like whatismyipaddress.com when accessed through Tor and a regular browser. The slower loading times in Tor are a consequence of the anonymization process, as data packets travel through multiple nodes.
Conclusion
The darknet represents a complex and often misunderstood part of the internet. While offering valuable anonymity for those seeking privacy and freedom of information, it also harbors illicit activities. Understanding how the darknet functions, particularly the role of Tor and its anonymization methods, is crucial for navigating this hidden realm.