As a seasoned IT security expert with over 30 years of experience, I’ve developed specific habits and principles to stay safe online. While these practices seem second nature to me, I often observe other users engaging in risky behaviors. So, I’ve compiled a list of 10 crucial things I would never do, along with safer alternatives.
1. Moving Files Instead of Copying
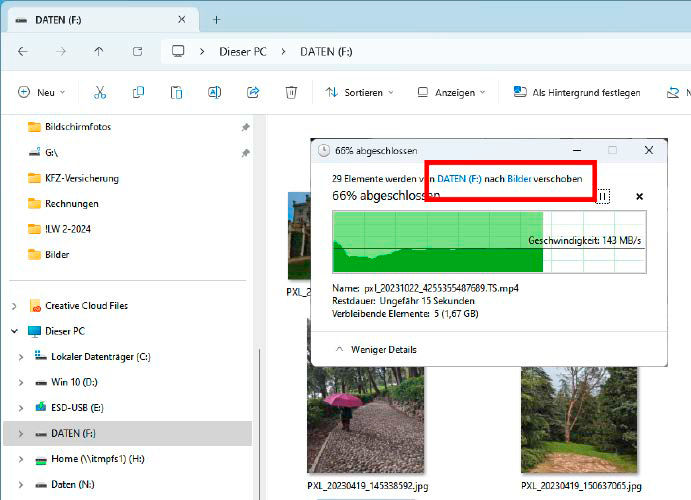 alt text: Moving files in Windows Explorer can be risky for data security. Always copy important files before moving them
alt text: Moving files in Windows Explorer can be risky for data security. Always copy important files before moving them
Moving unique files like photos and videos directly from cameras or smartphones feels inherently risky. While rare, data loss during transfer is possible. Even if the move is successful, your data exists in only one location, making it vulnerable to hard drive failures or accidental deletions. Copying these files first ensures redundancy.
If storage space is a concern, invest in additional storage like a second SD card. Back up your copied data to a secure location, such as a network drive or cloud storage, before deleting the originals. I personally use an encrypted hard drive connected to a Raspberry Pi for network backups and also utilize cloud storage for critical files.
2. Saving Data Without a Backup
 alt text: Data loss can occur due to various reasons, highlighting the importance of regular backups.
alt text: Data loss can occur due to various reasons, highlighting the importance of regular backups.
I always have an automatic backup system in place for all important data, including files created on my devices and information entered into apps across Android, iOS, and Windows. Even if apps lack obvious backup functionalities, users are responsible for their data’s safety.
The incident of data loss on school iPads in Koblenz, Germany, highlights the importance of backups. Hundreds of student notes were lost due to a network error, emphasizing the need for a secondary copy of data, whether through cloud services or other backup methods.
3. Formatting Storage Without Verification
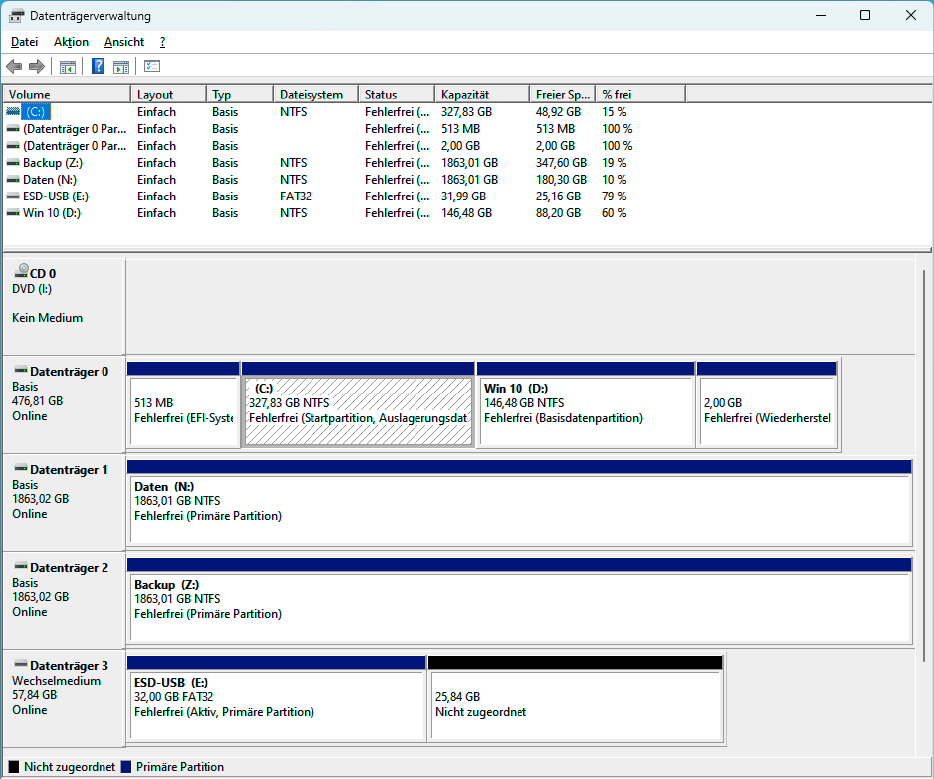 alt text: Windows Disk Management helps identify drives and partitions before formatting to prevent data loss
alt text: Windows Disk Management helps identify drives and partitions before formatting to prevent data loss
From personal experience, I strongly advise double-checking before formatting any storage device. I once formatted the wrong external hard drive due to similar naming conventions and drive letters. Since then, I clearly label all external drives and meticulously verify the correct drive before formatting.
Always confirm the drive letter in Windows Explorer and utilize Disk Management to identify drives and partitions accurately. Disconnecting other drives can further minimize confusion. Verifying the disk name and size also helps prevent accidental data loss.
4. Opening Links in Emails
 alt text: Avoid opening links in emails, especially from banks or payment providers, to prevent phishing attacks.
alt text: Avoid opening links in emails, especially from banks or payment providers, to prevent phishing attacks.
I avoid opening links in emails, especially those purportedly from banks or payment services. Even legitimate-looking emails can be sophisticated phishing attempts. Instead, I access online banking and other sensitive accounts via saved bookmarks or by manually typing the address into the browser.
I then check for any new messages within my account. If the information isn’t present on the official platform, the email is likely a phishing attempt or unimportant.
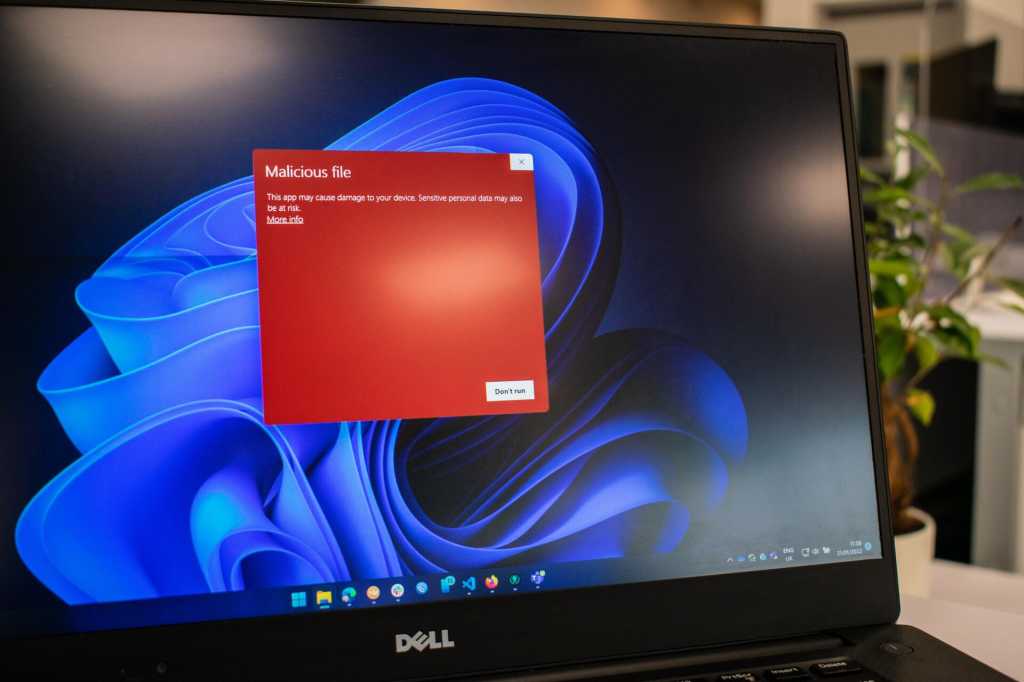
5. Opening Suspicious Files
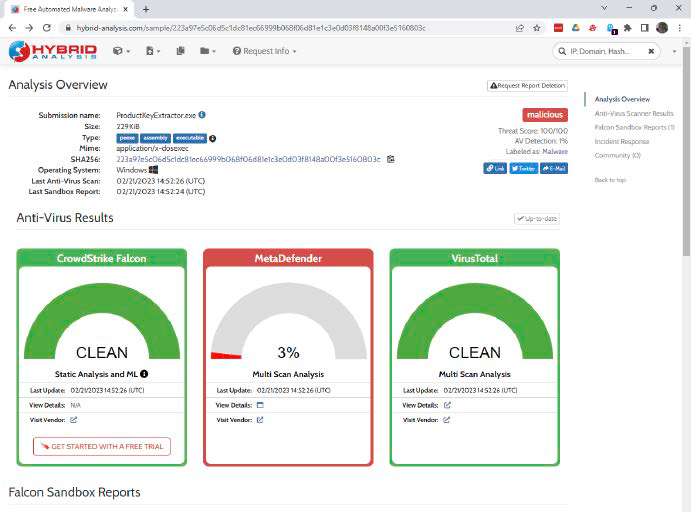 alt text: Use online sandboxes like Hybrid Analysis to analyze suspicious files and prevent malware infections.
alt text: Use online sandboxes like Hybrid Analysis to analyze suspicious files and prevent malware infections.
I never open suspicious files, whether programs or documents, due to the inherent risks. If I must handle such files, I first scan them using VirusTotal, which checks the file against multiple antivirus engines. For more in-depth analysis, online sandboxes like Hybrid Analysis provide a safer environment to examine the file’s behavior.
6. Paying for Services with Gift Cards
 alt text: Gift cards are a common payment method requested by scammers. Be wary of any service requesting payment via gift cards.
alt text: Gift cards are a common payment method requested by scammers. Be wary of any service requesting payment via gift cards.
Paying for services with gift cards is a common tactic used by scammers. Social engineering techniques exploit human psychology, using fear, trust, or ignorance to manipulate individuals. A common scam involves fake warnings claiming a hacked PC, urging victims to call a support number and purchase gift cards for payment. Always be suspicious of unusual payment requests like gift cards.
7. Connecting Unknown External Devices
 alt text: Avoid connecting unknown USB drives to prevent malware infections and data breaches.
alt text: Avoid connecting unknown USB drives to prevent malware infections and data breaches.
I never connect unknown USB drives to my devices. While Windows’ autostart functionality has improved, attackers can still exploit curiosity by using enticing file names. Infected USB drives can compromise systems and even entire networks, as demonstrated by the Stuxnet incident. If you must connect an unknown USB drive, scan its contents with VirusTotal or use a sandbox for analysis.
8. Using Default Passwords
 alt text: Dashlane password manager helps create and manage strong, unique passwords.
alt text: Dashlane password manager helps create and manage strong, unique passwords.
I always change default passwords on new devices and online accounts. Attackers exploit known default passwords to gain unauthorized access. A robust password manager, like Dashlane, is invaluable for creating and managing strong, unique passwords for all your accounts.
9. Enabling Unnecessary Network Services
 alt text: Disable unnecessary network services on devices like routers and webcams to minimize security vulnerabilities.
alt text: Disable unnecessary network services on devices like routers and webcams to minimize security vulnerabilities.
I disable any unnecessary network services on my devices, such as remote access to routers, smart lighting, NAS devices, and other connected appliances. Vulnerabilities in these services can expose your data and network to hackers.
10. Buying Premium Antivirus Versions
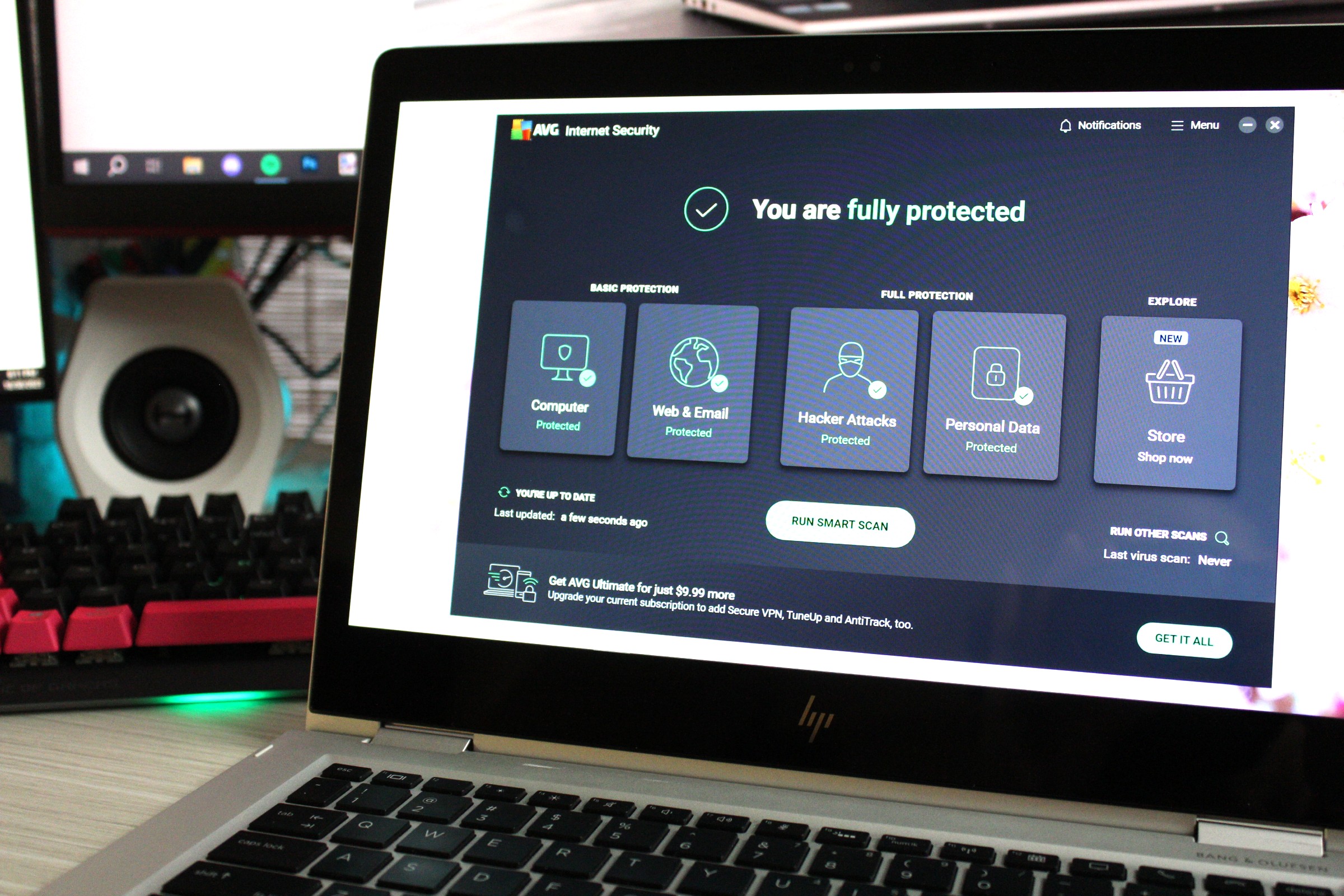 alt text: AVG Internet Security provides a good balance between features and price for antivirus protection.
alt text: AVG Internet Security provides a good balance between features and price for antivirus protection.
I typically opt for the mid-tier internet security suites instead of the most expensive premium antivirus versions. These offer a good balance of features and protection without the added cost of services I don’t necessarily need, such as metadata cleansing or social media monitoring. Often, these additional features can be obtained separately at a lower cost. AVG Internet Security is a good example of a budget-friendly option.