Apple’s Find My network, designed to locate lost devices, has a significant security vulnerability. Researchers at George Mason University have demonstrated how this network can be exploited to track virtually any Bluetooth device, expanding the potential for misuse far beyond AirTags or iPhones. This exploit leverages a combination of Apple’s network and a device’s Bluetooth address, raising serious privacy concerns.
The Find My network operates by having devices like AirTags emit Bluetooth signals that are picked up by nearby Apple devices and anonymously relayed to Apple’s cloud. This anonymity is the key to the exploit. Researchers have developed a method called “nRootTag,” which achieves a 90% success rate in tracking Bluetooth devices via the Find My network.
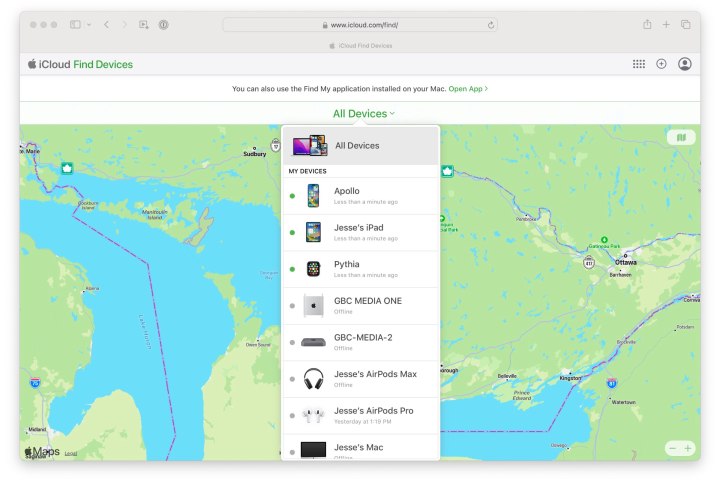 Researchers found a security flaw in Apple's Find My Network.
Researchers found a security flaw in Apple's Find My Network.
Since the Find My network relies on encrypted data instead of administrative privileges, the “nRootTag” method dynamically adapts an encryption key to track devices. This essentially turns any Bluetooth-enabled device into a trackable beacon without the owner’s knowledge or consent.
Real-World Implications of the Find My Exploit
The research team successfully tested the exploit on a range of devices, demonstrating its alarming effectiveness. They pinpointed a computer’s location within 10 feet and even tracked an airplane’s flight path by targeting a passenger’s gaming console.
This vulnerability extends the potential for misuse far beyond the issues previously seen with AirTags being used for unwanted tracking. The team easily tracked VR headsets, smart TVs, and other devices, highlighting the broad scope of this security flaw.
 Apple's Find My app icon.
Apple's Find My app icon.
Qiang Zeng, a member of the research team, emphasized the increased risk when location data is combined with device vulnerabilities, citing the example of a smart lock: “While it is scary if your smart lock is hacked, it becomes far more horrifying if the attacker also knows its location.”
Apple’s Response and Mitigation Strategies
The research team notified Apple of this vulnerability in July 2024. While Apple has acknowledged the issue, a patch has yet to be released. The complexity of the flaw, rooted in the core functionality of the Find My network, presents a significant challenge in developing a fix without compromising the network’s intended purpose. The research team estimates a patch could take years to implement.
In the interim, Junming Chen, the lead researcher, advises users to keep all devices and software updated and carefully scrutinize Bluetooth permissions requested by apps, especially those that don’t have an obvious need for Bluetooth access.
This research underscores the importance of ongoing security assessments and the need for vigilance in protecting personal privacy in an increasingly connected world. The “nRootTag” exploit highlights a significant vulnerability in Apple’s Find My network, emphasizing the potential for malicious actors to exploit seemingly innocuous technologies for harmful purposes. Until a patch is available, users must remain cautious and take proactive steps to mitigate potential risks.