The 2024 takedown of the darknet platform Boystown by German authorities raised concerns about the security of the TOR network. While this success is a positive step in combating online crime, it also prompts questions about the anonymity of TOR users, including journalists, activists, and those seeking access to information in restrictive environments. This article explores the current state of TOR security, alternative anonymity tools, and best practices for online privacy.
Understanding Online Anonymity and the Role of TOR
The TOR (The Onion Router) network has long been a symbol of online anonymity, enabling users to access the internet without revealing their IP address or location. It’s a crucial tool for individuals in countries with strict censorship and surveillance, as well as journalists and whistleblowers who rely on anonymity for their safety. However, the Boystown case highlights the evolving challenges to online privacy.
 TOR Browser icon app on the screen
TOR Browser icon app on the screen
Exploring Alternatives to TOR: Proxies and VPNs
While TOR remains a powerful tool, understanding alternative anonymity methods is crucial. Proxy servers act as intermediaries between your computer and the internet, masking your IP address. However, free proxies often come with limitations, such as slow speeds and potential logging of user data.
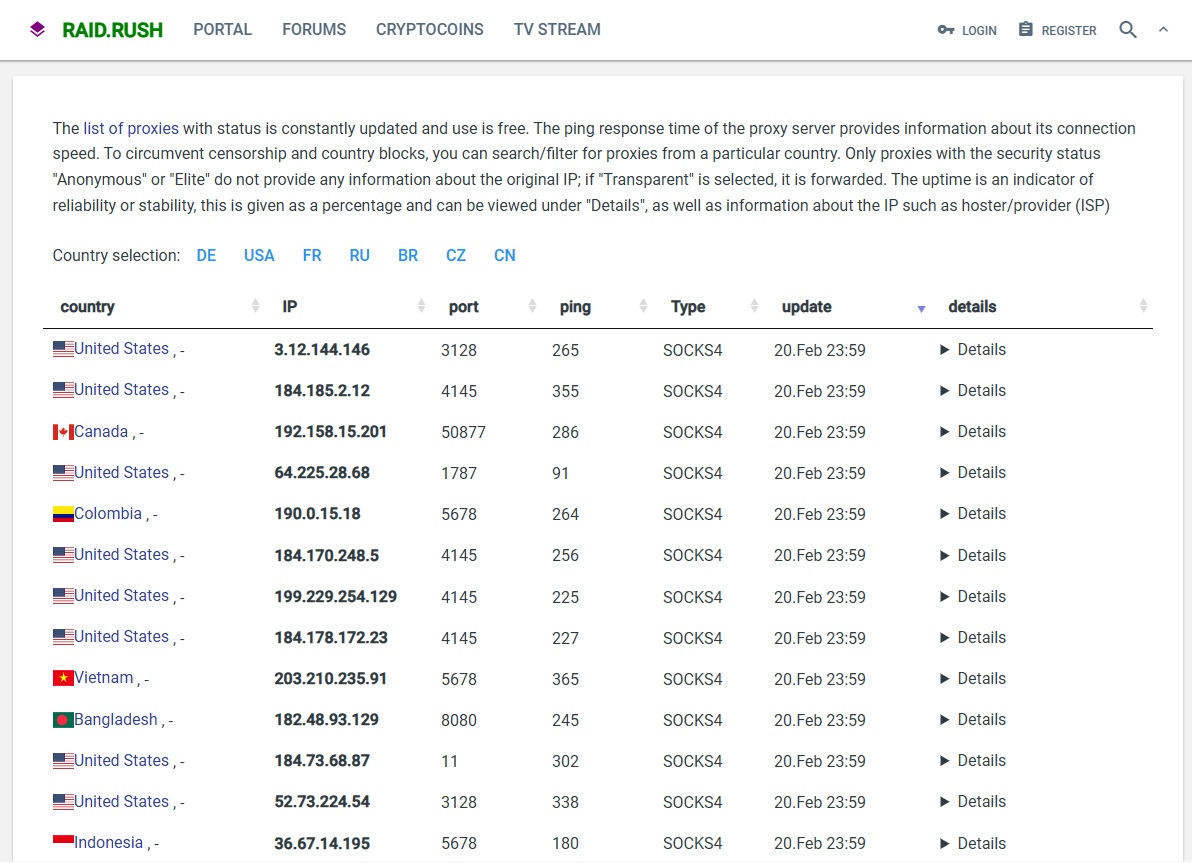 Raid Rush
Raid Rush
VPNs (Virtual Private Networks) offer a more robust solution, encrypting your internet traffic and routing it through a secure server. This protects all online activity, not just browsing. Paid VPN services generally provide better speed, security, and a no-log policy, ensuring your data remains private.
 Einige Proxydienste wie etwa Proxysite arbeiten auch mit Webseiten, bei denen Sie lediglich die gewünschte Zieladresse eintippen. So entfällt die Umkonfiguration des Browsers.
Einige Proxydienste wie etwa Proxysite arbeiten auch mit Webseiten, bei denen Sie lediglich die gewünschte Zieladresse eintippen. So entfällt die Umkonfiguration des Browsers.
Mullvad VPN: A Top Choice for Privacy
Mullvad VPN stands out with its strong commitment to privacy and security. Offering competitive pricing and a strict no-log policy, Mullvad is a reliable option for those seeking online anonymity.
 MullvadEditors
MullvadEditors
Beyond IP Addresses: Combating Fingerprinting and Tracking
Modern tracking methods go beyond IP addresses, utilizing fingerprinting to identify users based on their browser configuration, hardware, and software. Disabling JavaScript can mitigate this, but it also impacts website functionality. Some browsers offer built-in defenses against fingerprinting, providing inaccurate data or blocking known trackers.
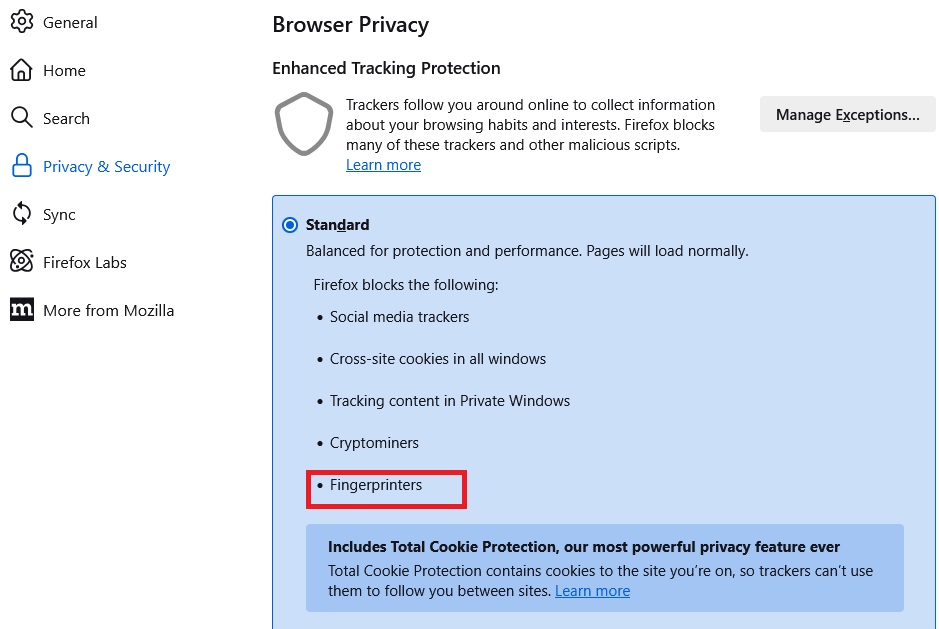 Firefox fingerprints
Firefox fingerprints
Cookies, particularly third-party cookies, are another common tracking tool. Managing cookie settings in your browser, including deleting them upon closing and utilizing the “Do Not Track” feature, can enhance your privacy.
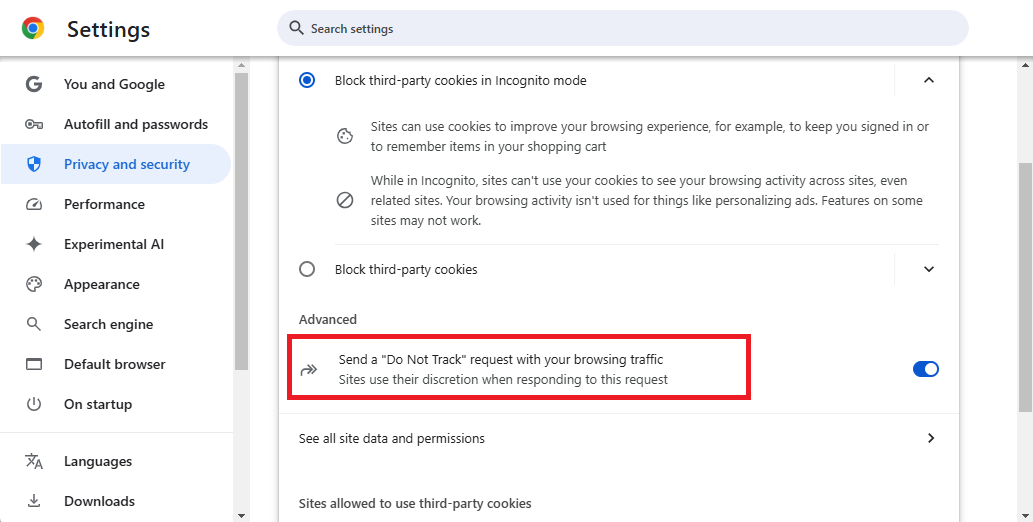 Do not track
Do not track
The Continued Relevance of TOR
Despite the Boystown case, TOR remains a highly secure anonymity tool for most users. Its multi-layered encryption and routing system provides strong protection against surveillance. The investigation’s success likely involved extensive resources and targeted monitoring, not a fundamental crack in TOR’s security.
Enhancing Privacy in Search and Mobile
Search engines like Google and Bing collect user data. Alternatives such as Startpage and DuckDuckGo prioritize privacy, offering anonymous searching without tracking your history or IP address. On mobile devices, consider privacy-focused operating systems like LineageOS or /e/OS, especially for older devices.
 Lineage-OS ist ein alternatives Betriebssystem für Android-Smartphones. Der Hersteller verspricht ein höheres Datenschutzniveau als beim Google-System.
Lineage-OS ist ein alternatives Betriebssystem für Android-Smartphones. Der Hersteller verspricht ein höheres Datenschutzniveau als beim Google-System.
Conclusion: A Multi-Layered Approach to Online Anonymity
Maintaining online privacy requires a comprehensive approach. While TOR remains a valuable tool, combining it with other strategies, such as VPNs, anti-fingerprinting measures, and privacy-focused search engines, provides a stronger defense against online tracking and surveillance. Choosing the right tools and practices depends on individual needs and risk tolerance.