A hacker typing on an Apple MacBook laptop while holding a phone. Both devices show code on their screens.Despite the common misconception that Macs are immune to malware, a new threat called Banshee Stealer is targeting Mac users, stealing sensitive data from browsers, crypto wallets, and even iCloud Keychain.
A hacker typing on an Apple MacBook laptop while holding a phone. Both devices show code on their screens.Despite the common misconception that Macs are immune to malware, a new threat called Banshee Stealer is targeting Mac users, stealing sensitive data from browsers, crypto wallets, and even iCloud Keychain.
What is Banshee Stealer and How Does it Work?
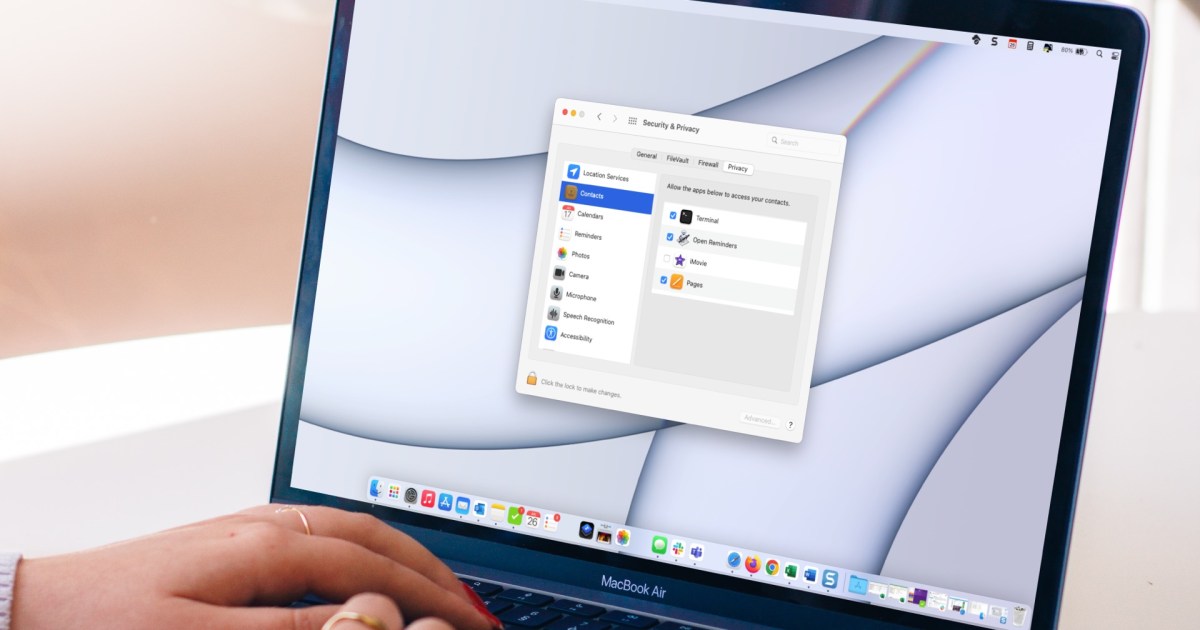
Banshee Stealer is a sophisticated malware designed to target macOS systems. It focuses on stealing data from popular browsers like Microsoft Edge, Google Chrome, and Mozilla Firefox, as well as cryptocurrency wallets such as Electrum, Coinomi, and Wasabi Wallet. The malware also attempts to extract data from iCloud Keychain passwords and Notes.
According to security firm Elastic Labs, Banshee Stealer targets “a wide range of browsers, cryptocurrency wallets, and around 100 browser extensions, making it a highly versatile and dangerous threat.” It collects a user’s browser history, cookies, login credentials, and more.
Evasive Techniques and Privilege Escalation
Banshee Stealer incorporates several techniques to evade detection and analysis by security researchers. One notable tactic is its use of the CFLocaleCopyPreferredLanguages API to identify the computer’s primary language. If set to Russian, the malware avoids infecting the system.
To gain escalated privileges, Banshee Stealer employs a deceptive tactic: displaying a fake password prompt after an app launch, urging the user to “update system settings” by entering their password. This allows the malware to capture user credentials, which it then verifies using the OpenDirectory API. Symantec, owned by Broadcom, further elaborates that after credential verification, the malware downloads and executes malicious scripts from a command-and-control server. Additionally, Banshee Stealer can extract information from various file types, including .txt, .docx, and .wallet files.
The High Cost of Banshee Stealer
Unlike many other malware variants, Banshee Stealer comes with a hefty price tag of $3,000 per month. Elastic Labs highlights this unusually high cost, particularly compared to similar malware targeting Windows systems. This suggests a potentially targeted approach, possibly focusing on users with valuable data or high-value assets.
Protecting Your Mac from Banshee Stealer and other Malware
While Banshee Stealer presents a significant threat, Mac users can take proactive steps to mitigate the risk:
- Exercise caution when downloading files: Be wary of downloading files from untrusted sources, including emails, messages, and unverified websites.
- Keep your Mac updated: Regularly install macOS updates, as they often include critical security patches that address vulnerabilities exploited by malware.
- Consider antivirus software: Employing reputable antivirus software can provide an additional layer of protection against malware threats.
Although Banshee Stealer is a serious concern, it serves as a reminder that no operating system is completely immune to malware. By staying vigilant and adopting preventative measures, Mac users can significantly reduce their risk of becoming a victim.