Protecting your online accounts with just a username and password is risky. Both can be easily stolen, guessed, or cracked. Two-factor authentication (2FA) significantly enhances security and is recommended for all important accounts. It’s even been mandatory for online banking for years.
2FA uses two factors from different categories for account access:
- Knowledge: (password, PIN)
- Possession: (smartphone, Fido2 key)
- Biometrics: (fingerprint, facial recognition)
Using more than two factors is called multi-factor authentication. While 2FA is robust, it isn’t foolproof. Hackers employ various tricks and exploit vulnerabilities to compromise accounts.
1. Man-in-the-Middle: 2FA Theft Through Phishing
Secure TLS (Transport Layer Security) connections protect communication between users and online accounts. However, “man-in-the-middle” attacks allow hackers to intercept this connection. Phishing is a primary threat to 2FA. Cybercriminals create fake websites mimicking legitimate services to steal login credentials. Victims are lured to these sites through deceptive emails, SMS messages, or WhatsApp messages.
Basic phishing pages steal login data. In a man-in-the-middle attack, the fake website also intercepts the 2FA code. The attacker then uses the stolen credentials and code for immediate access. This attack is time-sensitive, as one-time passwords (OTPs) are usually valid for only a few seconds.
While time-consuming for the attacker, the potential for direct financial gain makes it a persistent threat.
 This authentication app provides the corresponding one-time password for registered services. It is only valid for a few seconds before the app issues a new one.
This authentication app provides the corresponding one-time password for registered services. It is only valid for a few seconds before the app issues a new one.
2. Man-in-the-Browser: Malware Interception
Another “man-in-the-middle” variant involves malware embedded in the victim’s browser. The malware waits for the user to log in with 2FA, then manipulates transactions in the background. Examples of such malware include Carberp, Emotet, Spyeye, and Zeus.
The user sees the correct transaction details in their browser and authorizes them with the OTP. However, the malware secretly sends different recipient details and a larger amount to the bank.
Always meticulously verify transaction details, including the recipient’s IBAN, before authorizing with an OTP. Most banks re-send this information for confirmation.
3. Social Engineering: Tricking You Out of Your Code
Attackers may already possess your username and password from data breaches or through info-stealer malware. They then target the second factor by contacting you directly, often impersonating a bank employee. They might claim to be implementing a new security procedure, requiring your 2FA code for authorization. Providing the code grants them access to your account.
Never divulge 2FA codes to anyone, regardless of their claims. Legitimate service providers will never request this information.
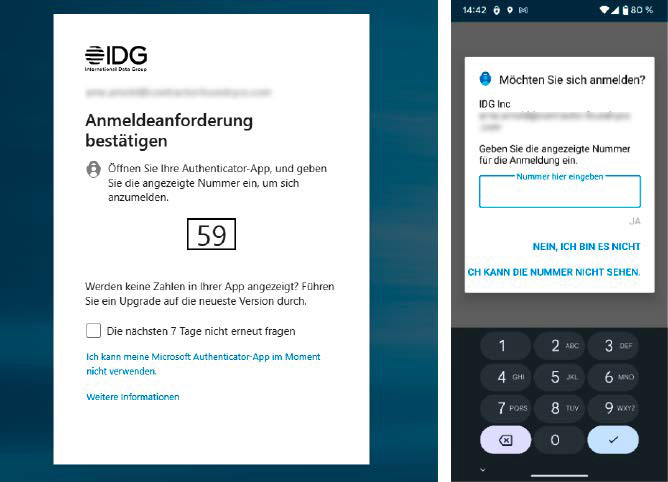 Here, a website (left) sends a push notification to the associated app on the smartphone. There, the user must now enter the displayed number to log into their account.
Here, a website (left) sends a push notification to the associated app on the smartphone. There, the user must now enter the displayed number to log into their account.
Tips for Secure Two-Factor Login
- Generate emergency codes, print them, and store them securely. Carry a few when traveling.
- Activate multiple 2FA methods (e.g., authentication app and hardware token) for backup.
- Avoid SMS-based 2FA for sensitive accounts due to SIM swapping vulnerability.
- Use an authentication app with backup functionality to transfer codes to a new device.
4. SIM Swapping: Hijacking Your Mobile Number
SMS-based OTPs were once considered secure but are now vulnerable to SIM swapping. The attacker gains control of your mobile number by convincing your provider to issue a new SIM card or eSIM, which they then activate to receive your OTPs. This is often achieved through deception, claiming a lost phone.
Avoid using SMS for 2FA. Opt for more secure methods like authentication apps or hardware tokens.
5. Malware Stealing Authentication Cookies
Many services offer the option to “remember” your browser, simplifying login after initial 2FA. This convenience increases vulnerability. The service stores an encrypted authentication cookie on your PC, which can be stolen by info-stealer malware like Lumma. The attacker then uses the cookie to access your account without needing login details or 2FA.
Use a reputable antivirus program and consider requiring 2FA for every login, even on trusted devices.
6. Insecure Backup Factors
Choosing a weak second factor, even as a backup, compromises security. While having multiple 2FA options is beneficial, attackers can exploit the weakest link. If you use both an authentication app and email-based OTPs, the attacker can target the less secure email option.
Prioritize secure factors like hardware tokens and app-based OTPs, and avoid insecure methods like SMS and email.
Overview of Two-Factor Authentication Methods
1. One-Time Passwords (OTPs)
- SMS-based OTPs: Sent to your phone via text message. Security: Low, vulnerable to SIM swapping and man-in-the-middle attacks.
- App-based OTPs: Generated by an authentication app. Security: Higher than SMS, but susceptible to phishing.
- Email-based OTPs: Sent via email. Security: Low, vulnerable to interception and phishing.
- Push Notifications: Sent to an authentication app requiring user confirmation. Security: Relatively high, but vulnerable to social engineering.
2. Hardware Tokens
- U2F/FIDO2 Tokens: USB or NFC-based hardware keys. Security: Very high, resistant to phishing and man-in-the-middle attacks.
 Hardware tokens as a second factor for logging in offer a high level of security and also work on smartphones.
Hardware tokens as a second factor for logging in offer a high level of security and also work on smartphones.
3. Passkeys
- Passkeys: An alternative to passwords. Security: High when used as a true second factor, but less secure when used as a password replacement.
4. Biometrics
- Fingerprint, etc.: Used for device unlocking or login. Security: Moderate, can be susceptible to spoofing.
Security Assessment and Recommendations
- Highest Security: Hardware tokens.
- Medium Security: Passkeys (as a second factor), app-based OTPs, push notifications, biometrics.
- Least Secure: SMS-based OTPs, email-based OTPs (avoid).