Despite advancements in junk mail filters and security measures, phishing remains a significant cyber security threat, evolving into increasingly sophisticated forms. Criminals now leverage Large Language Models (LLMs) like ChatGPT to craft convincing emails with impeccable grammar and natural sentence structure. This makes identifying these scams more challenging than ever. To stay ahead of these evolving threats, you need to be aware of the latest phishing tactics and equip yourself with effective detection methods. This article outlines several current phishing scams and provides practical tips to protect yourself.
Phishing Attacks Targeting AI Accounts
AI services like ChatGPT and Google Gemini are becoming indispensable for businesses, streamlining tasks like routine correspondence and invoicing. Consequently, providers like OpenAI and Google charge fees for usage beyond a certain threshold. This has created a new opportunity for cybercriminals.
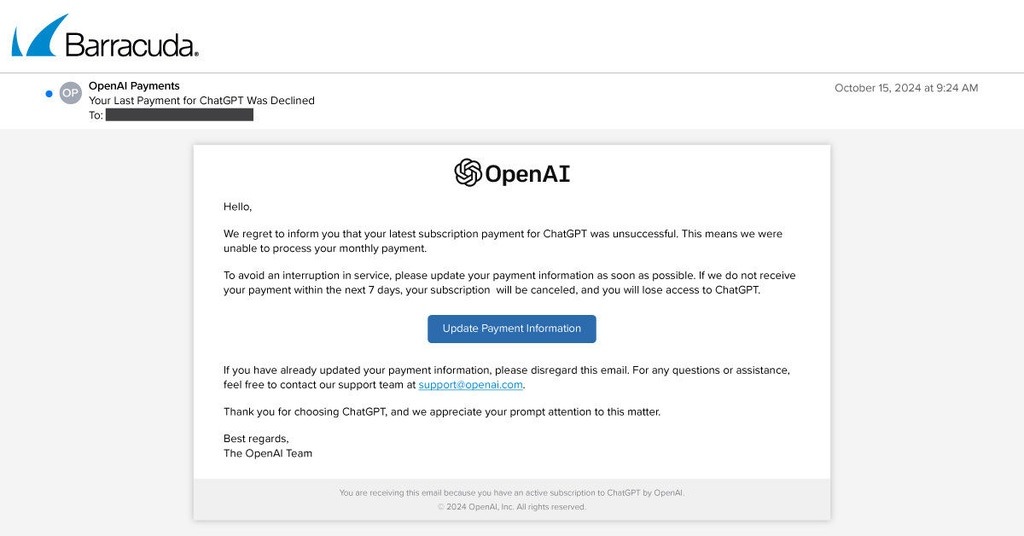
Barracuda Networks recently reported a widespread phishing campaign targeting paid ChatGPT accounts. These fraudulent emails, purportedly from OpenAI, claim an inability to process the monthly payment. Recipients are urged to update their account information within seven days to avoid losing access to ChatGPT. The provided link leads to a fake form designed to steal account credentials, which are then sold on the dark web.
Streaming Service Account Phishing
Streaming services like Netflix and Disney+ are also prime targets for phishing attacks. Recent months have witnessed waves of phishing emails requesting Netflix account data. These accounts are lucrative for criminals due to their ease of monetization.
These deceptive emails, disguised as official communication from streaming providers, prompt users to update their payment information to prevent account suspension. The included link directs victims to a counterfeit website with a form that captures their login credentials. Often, the fraudulent nature of these emails can be identified by carefully examining the sender’s address. However, some attackers employ “spoofing” techniques to forge legitimate email addresses. Hovering your mouse over any links or buttons will reveal the actual destination URL, helping you identify potential scams.
The Rise of Smishing
Smishing, a portmanteau of “SMS” and “phishing,” involves phishing attacks conducted via text message. A recent smishing wave utilizes the “grandchild trick.” The message typically reads: “Hi Dad, this is my new number. Can you write to me on WhatsApp?” Upon contact, the scammer fabricates a story about an accident or emergency, requesting a large sum of money to be transferred to a specified account.
Targeting Password Managers
Password managers, which store encrypted vaults of login credentials, are highly valuable targets for cybercriminals. Compromising the master password grants access to a treasure trove of sensitive information, from bank accounts and online shopping platforms to email and phone service accounts.
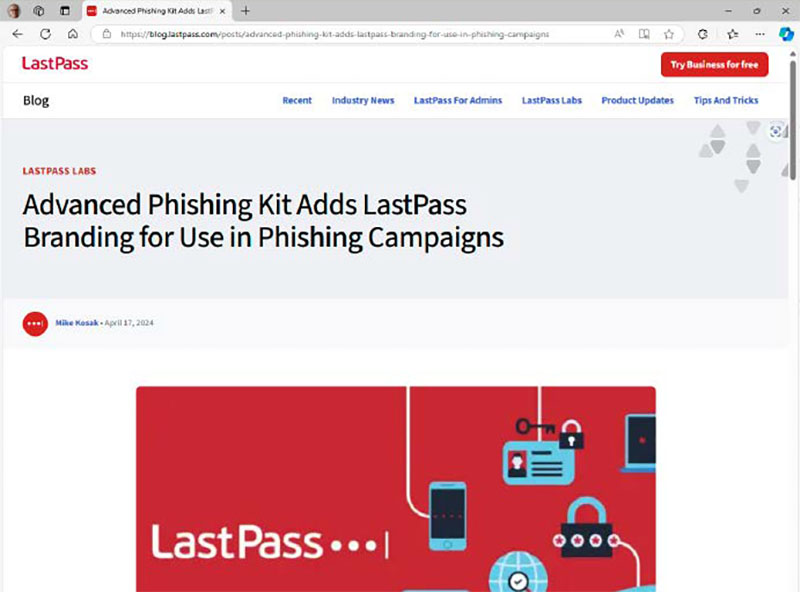
A new tactic emerged in spring 2024 involving phishing kits that simplify the creation of fake login pages, complete with authentic-looking company logos. These kits are offered online as part of “phishing-as-a-service” packages.
One example involves recreating the LastPass login page. The attackers then initiate automated calls, informing the recipient of an unauthorized login attempt. They are instructed to press “1” to authorize or “2” to block. Choosing “2” connects them to a fake customer service representative who requests their email address and sends a password reset email. This email links to a fraudulent website where the victim is tricked into entering their master password. Once obtained, the criminals change the account’s contact information, locking out the legitimate owner.
This method, known as “vishing” (voice phishing), employs high-pressure tactics to prevent victims from thinking critically. Given the sensitive data stored in password managers, implementing two-factor authentication or passkeys is highly recommended.
Exploiting Data Privacy Concerns
Cybercriminals are capitalizing on growing public awareness of data privacy regulations. Emails bearing the PayPal logo falsely claim account suspension due to unconfirmed information. To reactivate, the recipient is asked to enable “3DS Double Authorization,” a fabricated term resembling the legitimate 3D Secure. Clicking the link leads to a form requesting the victim’s phone number and PayPal login details. This information can then be used for further manipulation and fraudulent transactions.
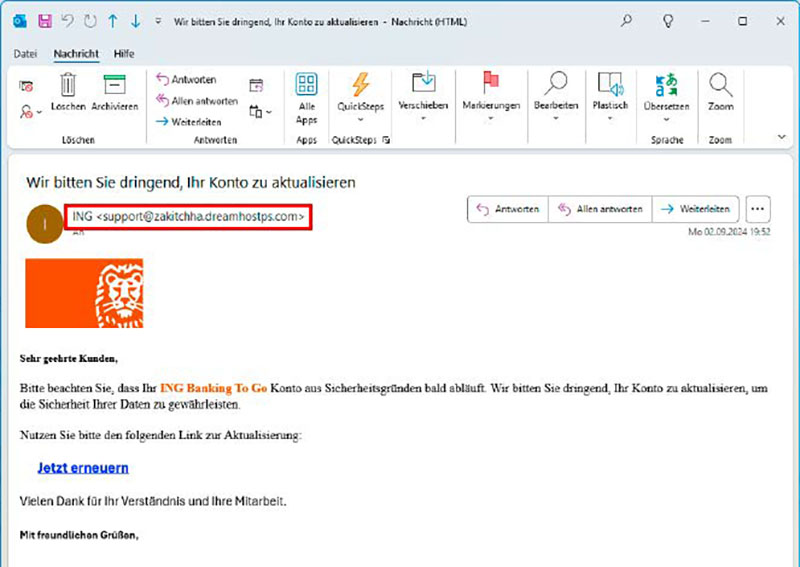
Identifying Phishing Emails: Key Indicators
Phishing attacks can lead to significant financial losses. Vigilance and careful scrutiny of incoming emails are crucial. Here are some key indicators:
-
Language Anomalies: While AI-generated phishing emails are more grammatically correct, they can still contain subtle errors. Be wary of unusual phrasing, foreign language snippets, incorrect salutations, and strange word choices.
-
Urgency and Pressure Tactics: Phishing emails often create a sense of urgency, demanding immediate action with threats of financial penalties or account suspension. The shorter the timeframe, the higher the likelihood of a phishing attempt.
-
Suspicious Links and Buttons: Hover your mouse over links and buttons (without clicking) to reveal the actual destination URL. If it doesn’t match the purported sender’s website, it’s likely a phishing attempt.
-
Online Verification: Search online for the subject line or key phrases from suspicious emails. This can reveal if others have received similar messages and reported them as phishing attempts.
If you suspect a phishing email, delete it immediately without responding. Staying informed about the latest phishing tactics is the best defense against these evolving cyber threats.