We rely on USB-C cables daily for data transfer and charging, often without a second thought. However, malicious USB-C cables can pose a significant security risk, going beyond simple data transfer to potentially compromise your devices. While these threats were once rare and expensive, they’ve become increasingly accessible, making it crucial to understand how to identify and protect yourself against them.
The Hidden Dangers of Malicious USB-C Cables
Malicious USB-C cables conceal embedded hardware capable of intercepting data, eavesdropping on communications, or even taking control of your computer or phone. While the first instances appeared in 2008, their prevalence has grown significantly, with both specialized retailers and unscrupulous sellers offering them, increasing the risk of accidental purchase and subsequent compromise.
Identifying Malicious Cables: A Challenge
Distinguishing a malicious USB-C cable from a legitimate one is difficult, as they are designed to appear identical. Advanced scanning techniques, like those employed by Lumafield, a leading industrial scanning company, offer the most reliable method of detection.
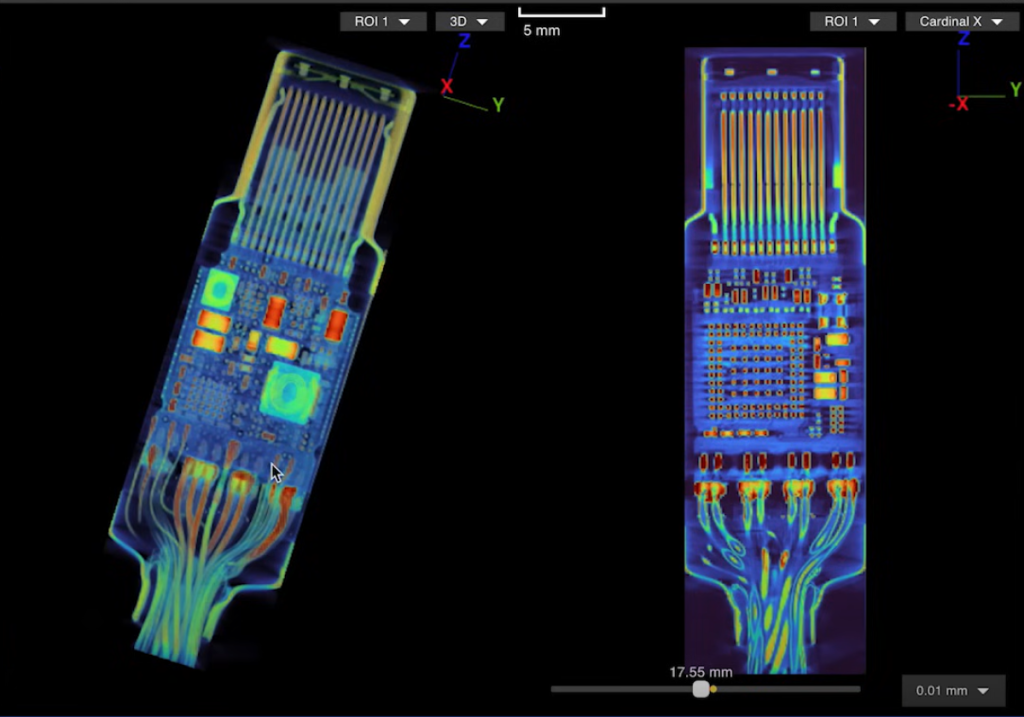
Lumafield’s analysis of the O.MG USB-C cable, a known malicious cable designed for covert use and research, revealed the power of 3D scanning. While 2D X-ray imaging identified the antenna and microcontroller, only a 3D CT scan uncovered a hidden set of wires connected to a die atop the microcontroller. This highlights the sophisticated nature of these malicious devices and the difficulty in detecting them without specialized equipment. You can explore Lumafield’s 3D model of the O.MG cable on their website.
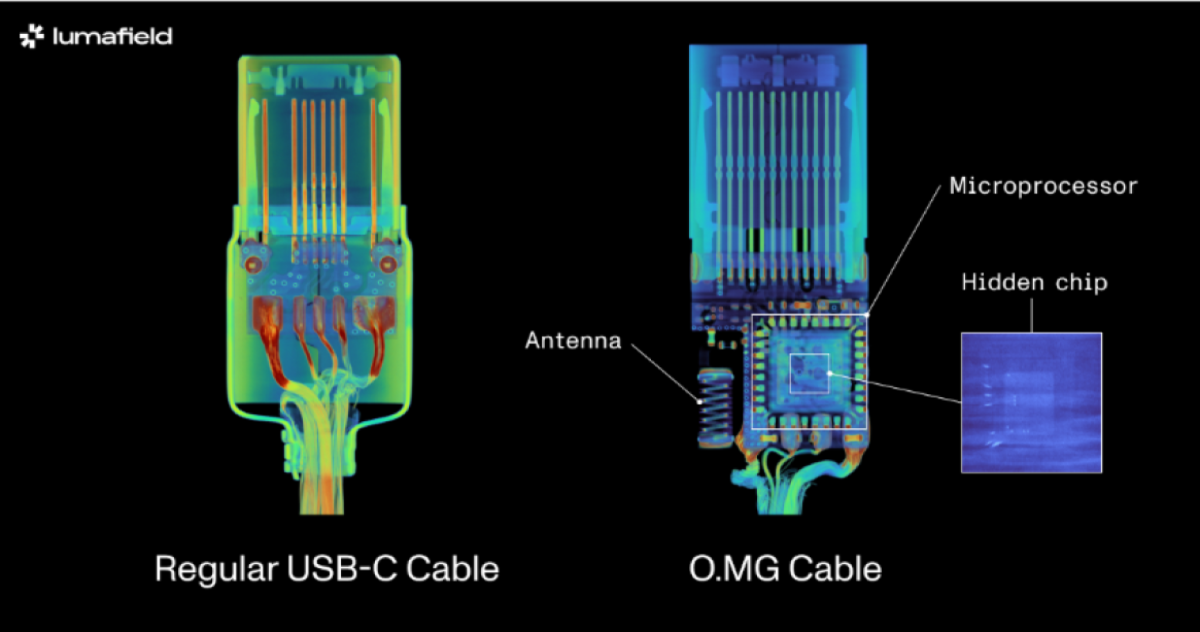 Malicious USB-C
Malicious USB-C
Practical Tips for Protecting Yourself
While access to 3D CT scanners is limited, there are practical steps you can take to minimize your risk:
Choose Reputable Sellers
Purchase USB-C cables from trusted brands like Anker, Apple, Belkin, and Ugreen. These manufacturers implement strict quality control, minimizing the risk of malicious components. Additionally, reputable brands often deliver superior product quality and performance.
Look for Warning Signs
Be wary of unusual brand markings, inconsistent cord lengths or widths, and USB-C connectors emitting heat when unplugged. These could indicate a malicious cable.
Utilize Detection Tools
Consider using the O.MG malicious cable detector, which claims to identify malicious USB cables.
Employ Data Blockers
When charging without data transfer, a data blocker can prevent data extraction. The O.MG cable detector also functions as a data blocker.
Consider Professional Detection Services
For businesses or government organizations handling highly sensitive data, professional detection services like those offered by Lumafield provide 100% accuracy. While these services come at a cost, they offer invaluable security and peace of mind.
Conclusion: Staying Safe in a Connected World
Malicious USB-C cables represent a real and growing threat. By understanding the risks and implementing these preventative measures, you can protect your data and devices from potential compromise. Sharing this information with others can contribute to a safer digital environment for everyone.