Operating systems require regular maintenance for optimal performance. While Windows includes some built-in tools, Microsoft offers a powerful suite of free utilities known as Sysinternals for advanced analysis, maintenance, and troubleshooting. These tools cater to both everyday users and IT professionals facing specific challenges. This article will guide you through using Microsoft Sysinternals to effectively maintain, analyze, and resolve issues within your Windows system.
Accessing and Setting Up Sysinternals
Sysinternals, originally developed by Mark Russinovich and Bryce Cogswell for their company Winternals Software LP, was acquired by Microsoft in 2006. These continually updated tools are compatible with modern Windows versions like Windows 10 and 11. They offer both graphical user interfaces and command-line options via PowerShell or the command prompt. You can download individual tools or the entire Sysinternals Suite from the Microsoft website.
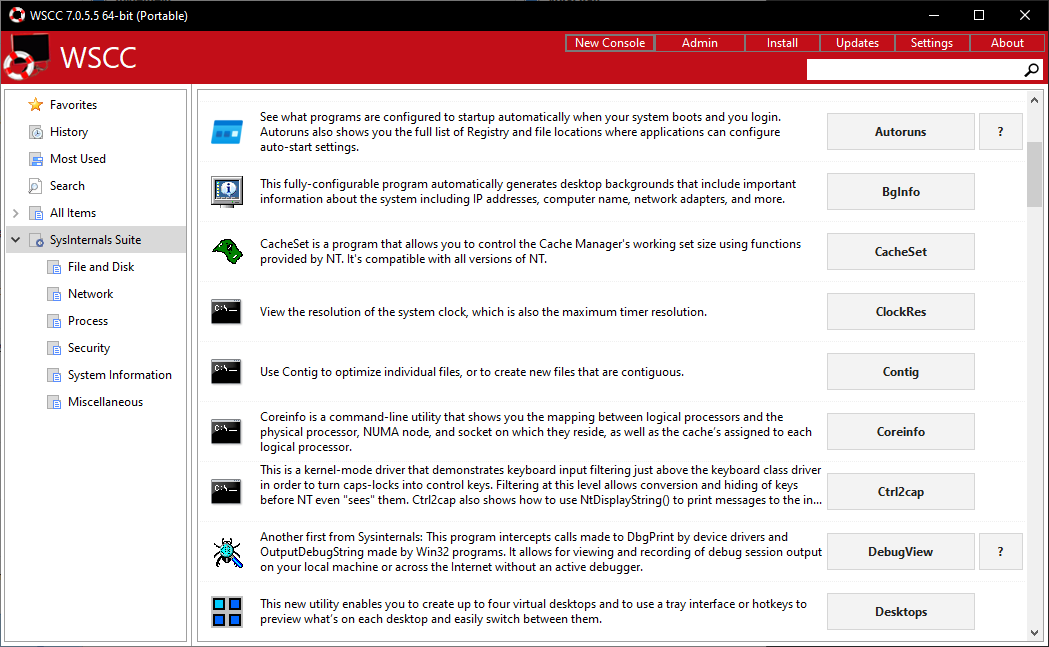 Set up Sysinternals tools conveniently: The Windows System Control Center (WSCC) downloads the tools and provides short descriptions.
Set up Sysinternals tools conveniently: The Windows System Control Center (WSCC) downloads the tools and provides short descriptions.
For simplified installation and updates, we recommend the Windows System Control Center (WSCC). Install WSCC in a short, simple folder path (e.g., “C:WSCC” or “C:ToolsWSCC”) for easier command-line access. Upon launching WSCC, select the desired tool packages under “Software Sources” and specify the installation path (the default “.SysInternals Suite” is usually sufficient). WSCC categorizes the tools for easy navigation and provides launch buttons and help file access. For 64-bit systems, enable “Launch the 64-bit version if available” in WSCC’s “General” settings.
Command-Line Configuration
To use Sysinternals tools directly from the command line without specifying the full path, add the installation directory to your system’s environment variables. Search for “environment variables” in Windows Settings, click “Edit environment variables for this account,” select “Path” under “User variables,” click “Edit,” and add the Sysinternals directory using “New.”
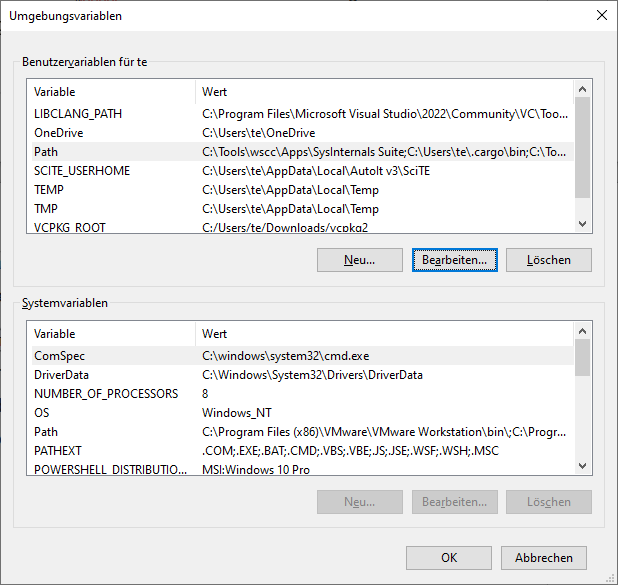 Configuration for the command line: So that the tools can be started in the Powershell or command prompt without specifying a path, configure the environment variable “Path”.
Configuration for the command line: So that the tools can be started in the Powershell or command prompt without specifying a path, configure the environment variable “Path”.
Process Explorer: Analyzing Running Processes
Windows Task Manager (Ctrl+Shift+Esc) provides a basic overview of running applications. Process Explorer (procexp.exe, procexp64.exe) offers a more comprehensive view, highlighting newly started processes in green and terminating processes in red. Sort processes by name, CPU usage, or memory consumption (“Private Bytes”) to identify resource-intensive applications.
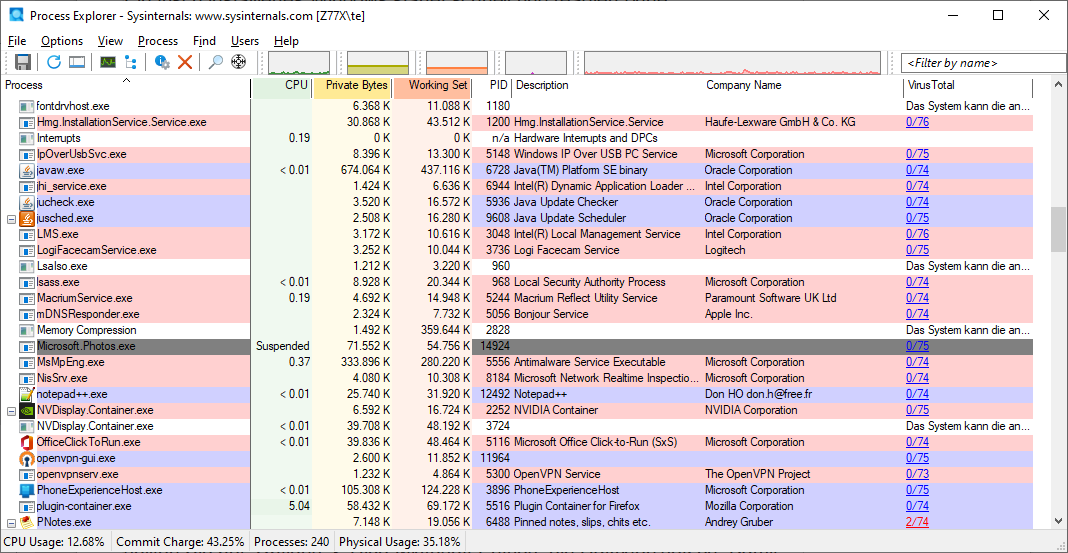 Process Explorer: The tool shows all running processes with names and descriptions and provides information on CPU load and memory requirements.
Process Explorer: The tool shows all running processes with names and descriptions and provides information on CPU load and memory requirements.
The “Properties” dialog for each process displays performance graphs for CPU, memory, and GPU usage, along with network resource access under the “TCP/IP” tab. Kill or restart processes using the context menu (administrator rights may be required).
Identifying Suspicious Processes
For unknown processes, “Search Online” performs a web search, while “Check Virustotal.com” scans the process against multiple antivirus engines. The “VirusTotal” column displays the scan results. Investigate processes flagged by multiple scanners on VirusTotal’s website for potential malware.
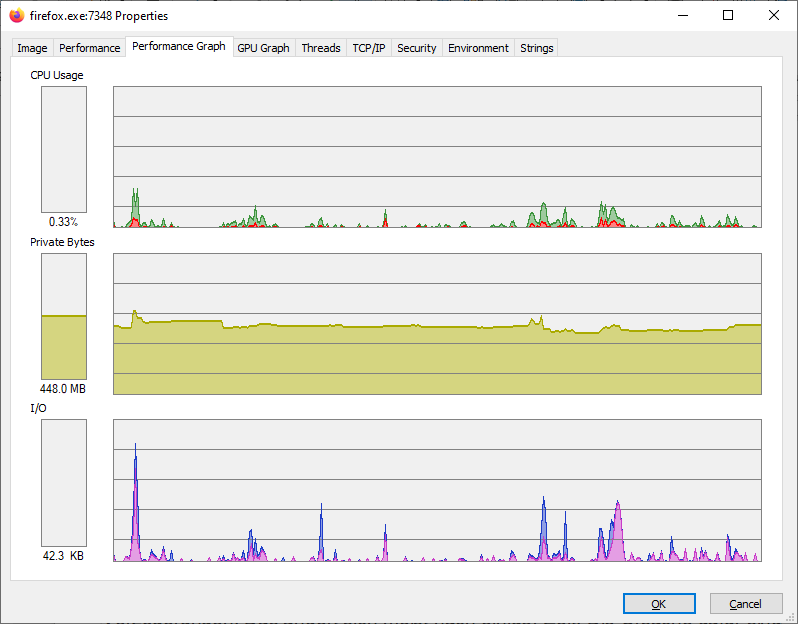 Performance history: The “Properties” of a process can be used to observe how processor load, memory requirements and hard disk accesses (“I/O”) develop.
Performance history: The “Properties” of a process can be used to observe how processor load, memory requirements and hard disk accesses (“I/O”) develop.
Autoruns: Managing Startup Programs
Over time, installed programs often add themselves to the system startup, impacting boot times and performance. Autoruns (autoruns.exe, autoruns64.exe) helps manage these startup entries, including Explorer and Office extensions.
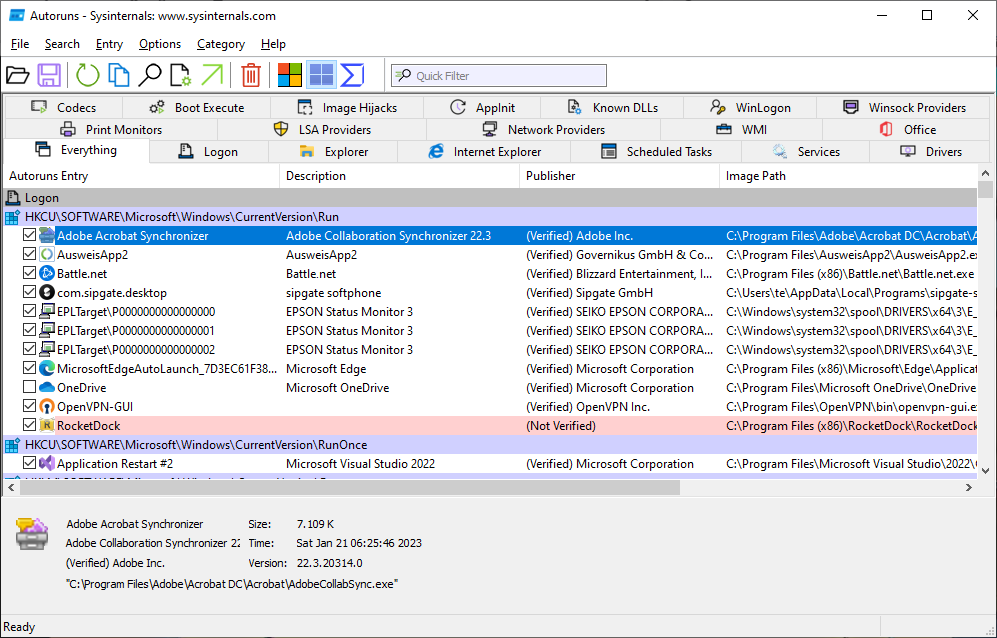 Automatic starts under control: Autoruns shows all autostart ramps. For programs you do not need, simply remove the tick in front of their name.
Automatic starts under control: Autoruns shows all autostart ramps. For programs you do not need, simply remove the tick in front of their name.
The “Everything” tab provides a comprehensive list, while “Options -> Hide Microsoft Entries” filters out Microsoft software. Uncheck unnecessary entries to disable startup (without deleting them). Run Autoruns as administrator to modify system services (exercise caution when disabling services).
Saving and Comparing Startup Configurations
Save your Autoruns configuration for future comparison. Use “File -> Compare” to highlight new or removed startup entries. “Search Online” and VirusTotal integration helps identify unknown or suspicious entries.
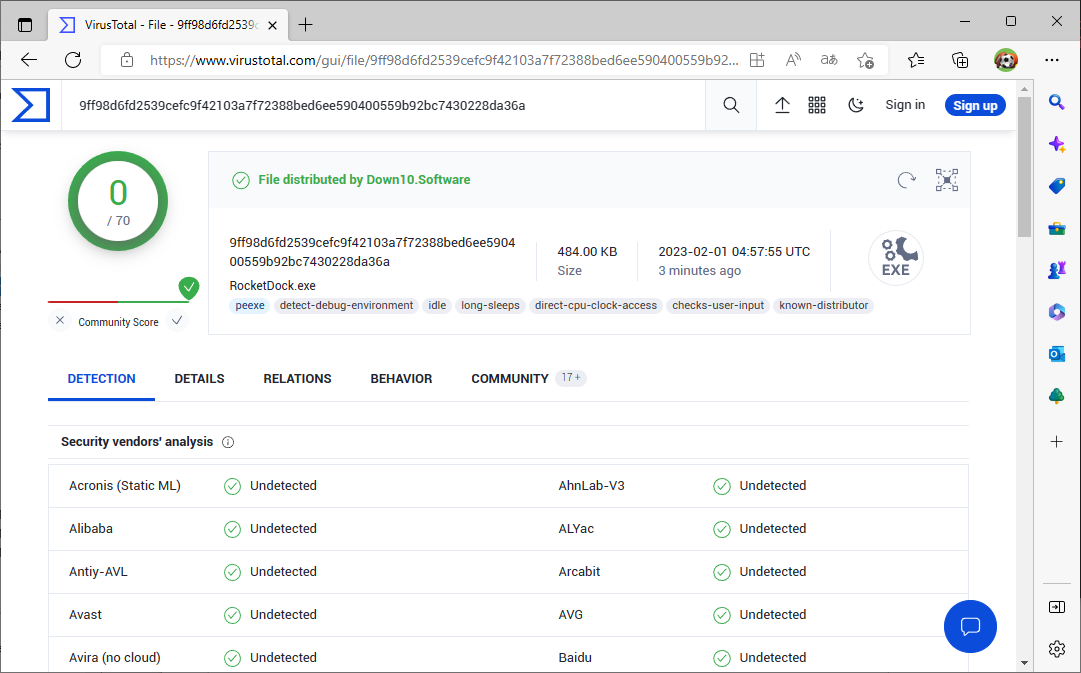 Check security: Send suspicious files to Virustotal.com. The result shows whether one or more virus scanners find malware in the file.
Check security: Send suspicious files to Virustotal.com. The result shows whether one or more virus scanners find malware in the file.
Process Monitor: Deep Dive into Program Behavior
Process Monitor (procmon.exe, procmon64.exe) captures real-time file system, registry, and network activity, allowing you to analyze program behavior and identify potential issues. Use filters to isolate specific processes or event types. The “Include Process from Window” feature simplifies filtering by selecting a specific application window. Analyze the captured events to understand resource access patterns.
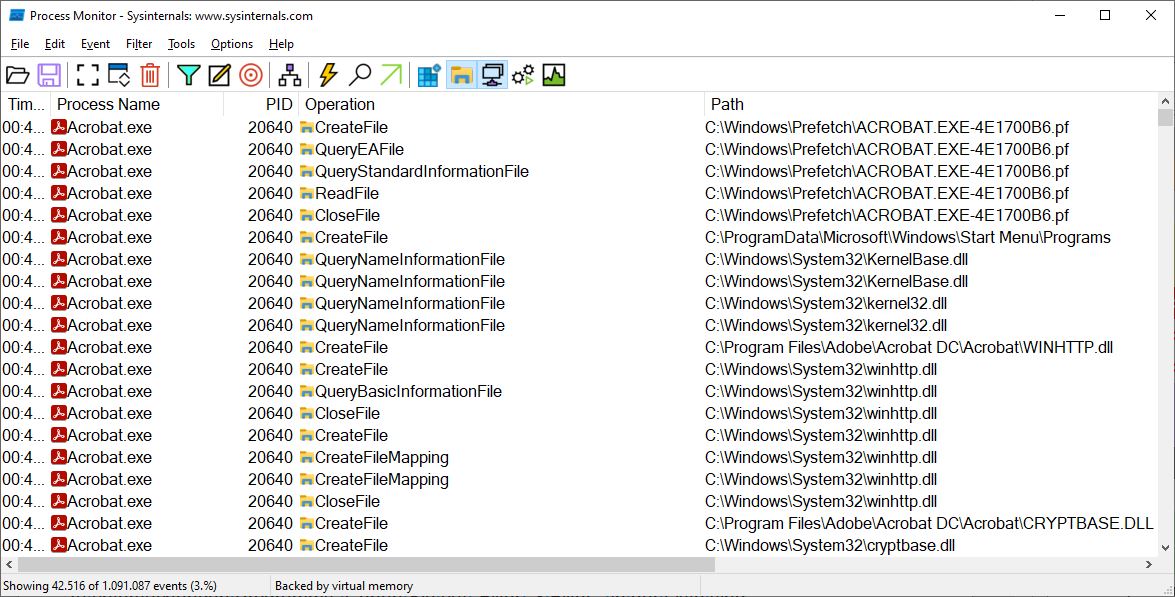 Process Monitor: The tool shows which system resources a program is accessing. For example, registry, file and network accesses can be determined.
Process Monitor: The tool shows which system resources a program is accessing. For example, registry, file and network accesses can be determined.
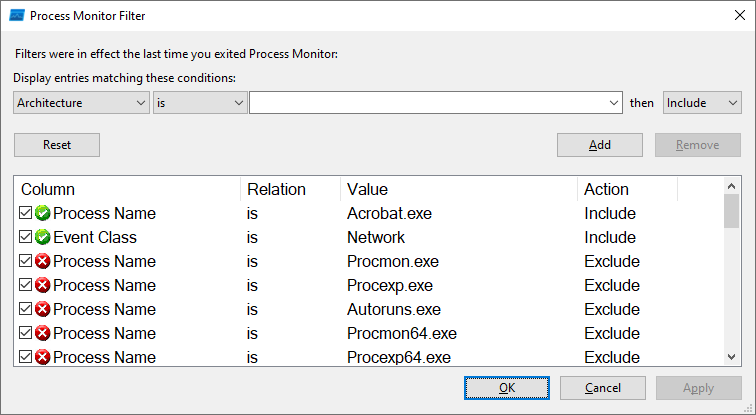 Create a filter for Process Monitor: Use a filter to restrict logging to events that are important to you, such as network access.
Create a filter for Process Monitor: Use a filter to restrict logging to events that are important to you, such as network access.
Sysmon, another Sysinternals tool, offers system-wide event logging for security auditing.
PS Tools: Remote System Administration
The PS Tools are command-line utilities for managing processes, shutting down systems, and performing other administrative tasks, both locally and remotely. The Pstools.chm help file provides detailed information.
 Help for PS-Tools: The help file Pstools.chm contains descriptions of the tools and explanations for the meaning of the available command line options.
Help for PS-Tools: The help file Pstools.chm contains descriptions of the tools and explanations for the meaning of the available command line options.
To enable remote access, configure the target PC by running the following commands in an elevated command prompt and restarting:
sc config RemoteRegistry start=auto
sc start RemoteRegistry
reg add HKLMSOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystem /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /fEnsure network share access and file and printer sharing are enabled.
Use the following syntax for remote execution:
tool.exe [IP] -u [user] -p [password] [options]For example, to open a remote PowerShell session:
psexec [IP] -u [user] -p [password] powershell.exeTo restart a remote PC after 10 seconds:
psshutdown -r -t 10 [IP] -u [user] -p [password]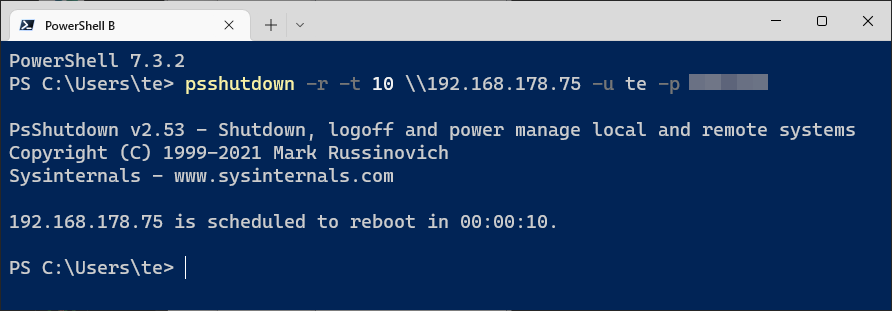 Remote shutdown: With the tool Psshutdown, a PC can be restarted via the network. The target PC must be configured for remote access.
Remote shutdown: With the tool Psshutdown, a PC can be restarted via the network. The target PC must be configured for remote access.
Handle: Resolving Locked Files and Folders
Handle Viewer (handle.exe, handle64.exe) identifies which processes are locking files or folders, preventing deletion, renaming, or drive ejection. Run Handle Viewer as administrator and specify the locked file/folder path:
handle C:MyFolderThe output displays the locking process, its ID, and the handle ID. Close the locking program or use the following command to close the handle directly (potential data loss for unsaved files):
handle -p [Process ID] -c [Handle ID]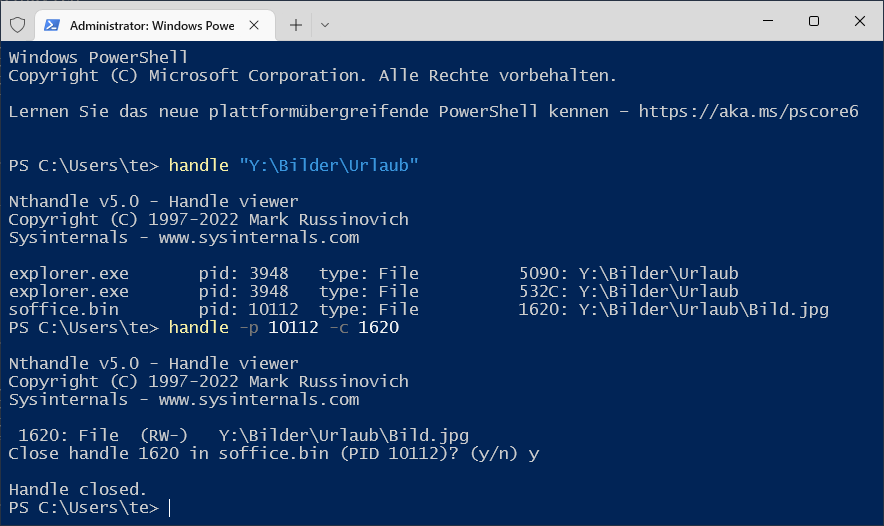 Who is blocking a file? Handle shows which process has just opened a file exclusively. If necessary, the file handle can also be closed.
Who is blocking a file? Handle shows which process has just opened a file exclusively. If necessary, the file handle can also be closed.