Windows, like most operating systems, relies on a centralized database called the registry to store system and application configurations. Every setting change, from desktop themes to application preferences, modifies corresponding registry values. This intricate system also holds values not accessible through conventional configuration tools, offering advanced users greater control over their Windows experience. This guide delves into the workings of the Windows registry, providing insights into its structure, navigation, and safe modification.
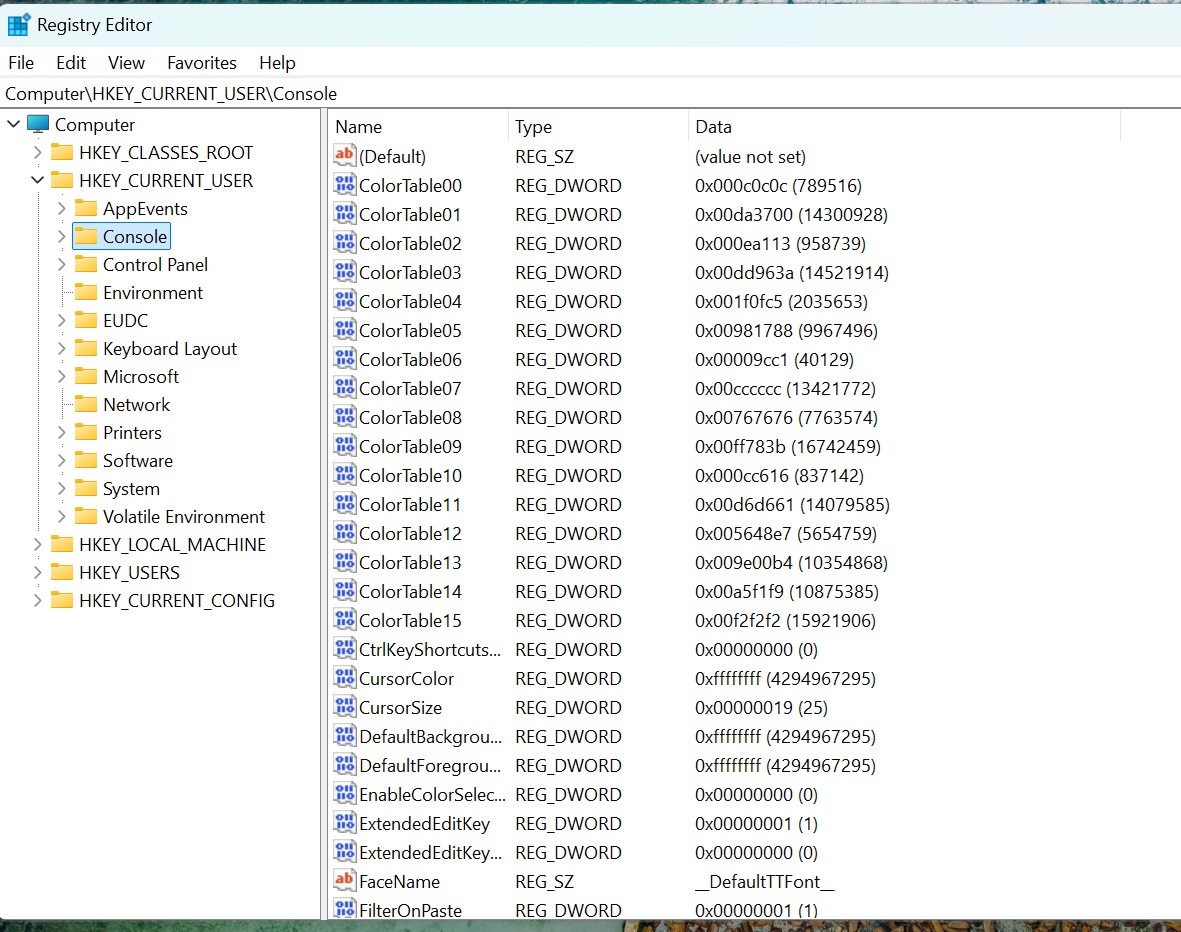 registry editor
registry editor
Navigating the Registry Landscape
The primary tool for interacting with the registry is the Windows Registry Editor. Launch it by pressing Win + R, typing regedit, and clicking “OK.” The editor presents the registry’s hierarchical structure in a familiar tree view. The registry comprises several files residing in C:WindowsSystem32config, along with Ntuser.dat in the user profile (C:Users[username]), containing user-specific settings.
Understanding the Registry Hierarchy
The registry is organized into five main branches, or hives:
- HKEY_CURRENT_USER (HKCU): Stores configuration settings for the currently logged-in user.
- HKEY_LOCAL_MACHINE (HKLM): Contains global settings for Windows and applications, requiring administrative privileges to modify. Changes typically take effect after a system restart.
- HKEY_USERS: Holds keys with user IDs of system profiles, including the current user, mirroring the content of HKCU.
- HKEY_CLASSES_ROOT (HKCR): Manages file associations, program shortcuts, and registered Windows components.
- HKEY_CURRENT_CONFIG: Acts as a shortcut to keys within
HKLMSystemCurrentControlSetHardware ProfilesCurrent, providing faster access for applications.
Keys and Values
Registry hives contain subkeys, analogous to folders in a file system. These subkeys hold values, comparable to files. Values have specific data types, such as “string” for text and “DWORD (32-bit)” for numeric data. To modify a value, select the corresponding key, double-click the value on the right pane, and enter the new data in the editor.
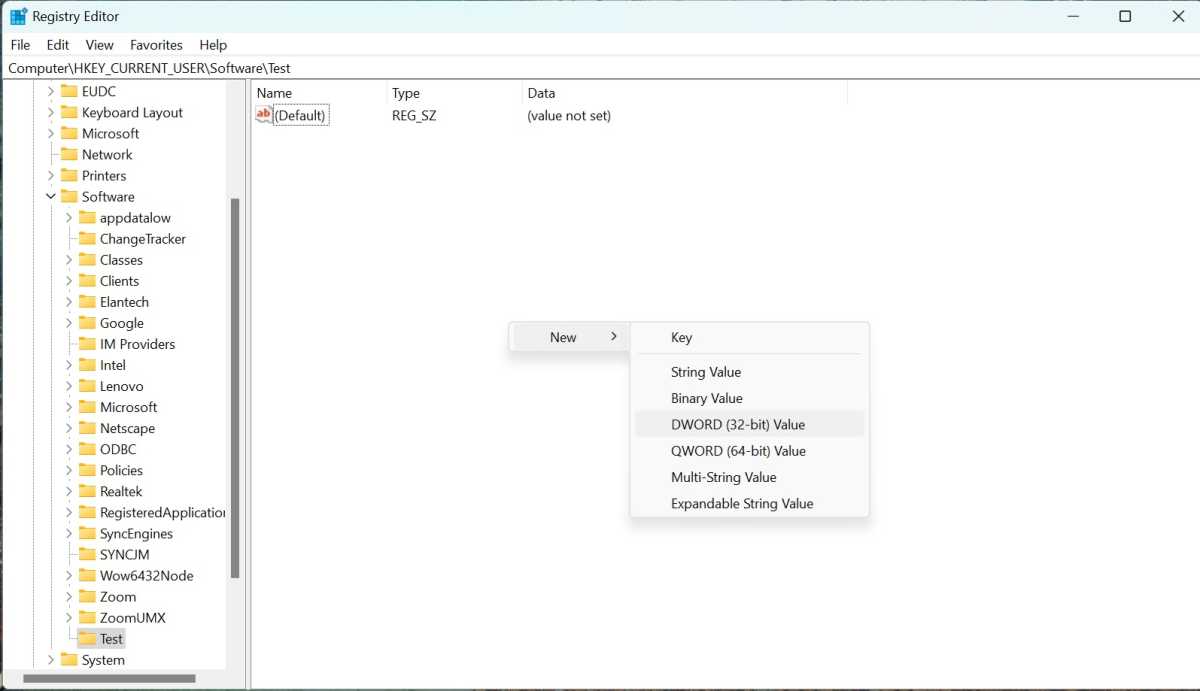 Registry Editor
Registry Editor
Safeguarding Your Registry: Backups and Restoration
Before making any registry changes, creating a backup is crucial. Registry Backup Portable is a recommended tool for this purpose. Configure the backup location in the program’s settings, then navigate to the “Backup Registry” tab and click “Backup Now.”
Restoring from a Backup
If any issues arise after modifying the registry, launch Registry Backup Portable, go to the “Restore Registry” tab, select the desired backup, and click “Restore Now.” A system restart is required to apply the restored settings.
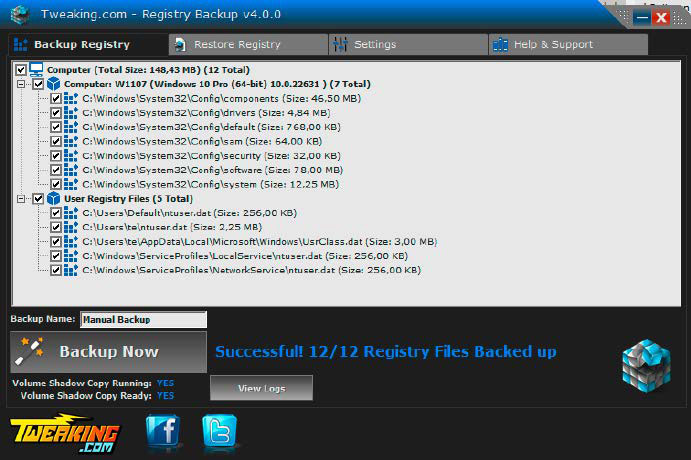 Registry Backup Portable: Mit dem Tool erstellen Sie eine vollständige Sicherungskopie aller Registry-Dateien. Bei Problemen stellen Sie die Dateien wieder her.
Registry Backup Portable: Mit dem Tool erstellen Sie eine vollständige Sicherungskopie aller Registry-Dateien. Bei Problemen stellen Sie die Dateien wieder her.
Analyzing Registry Activity with Process Monitor
Identifying the specific registry values associated with a particular setting can be challenging. Microsoft’s Process Monitor provides a powerful solution. Upon launching, configure a filter for “Operation” “is” “RegSetValue” and “Path” “begins with” “HKCU”. This focuses the monitoring on relevant changes.
Start recording, modify the desired setting, and stop recording immediately using Ctrl + E. The resulting log reveals the registry keys and values written during the setting change, though pinpointing the exact entry may still require careful analysis.
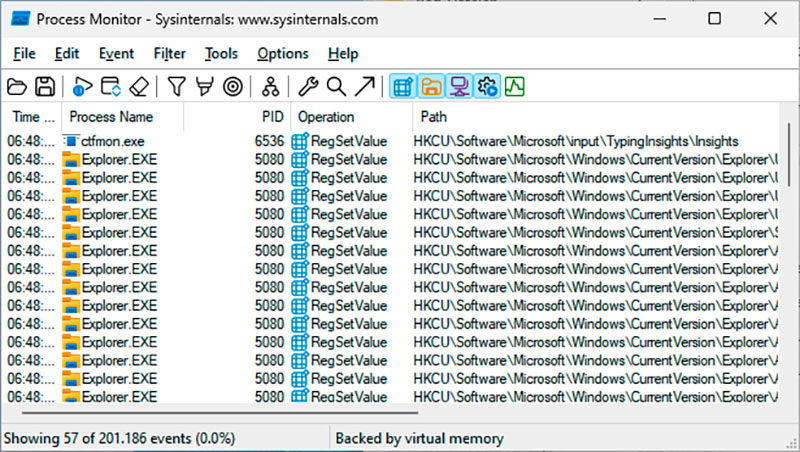 Registry überwachen: Process Monitor zeichnet ausgewählte Zugriffe in der Registry auf. Damit lässt sich kontrollieren, welche Werte sich bei einer Aktion ändern.
Registry überwachen: Process Monitor zeichnet ausgewählte Zugriffe in der Registry auf. Damit lässt sich kontrollieren, welche Werte sich bei einer Aktion ändern.
Practical Example: Customizing File Explorer
A common registry tweak involves displaying file name extensions in File Explorer. While Windows provides a visual representation of file types, explicitly showing extensions enhances clarity and security. Enable this setting through “View” > “Show” > “File name extensions” in File Explorer.
This seemingly minor change offers significant benefits, facilitating file type identification and preventing accidental execution of malicious files disguised with misleading extensions.
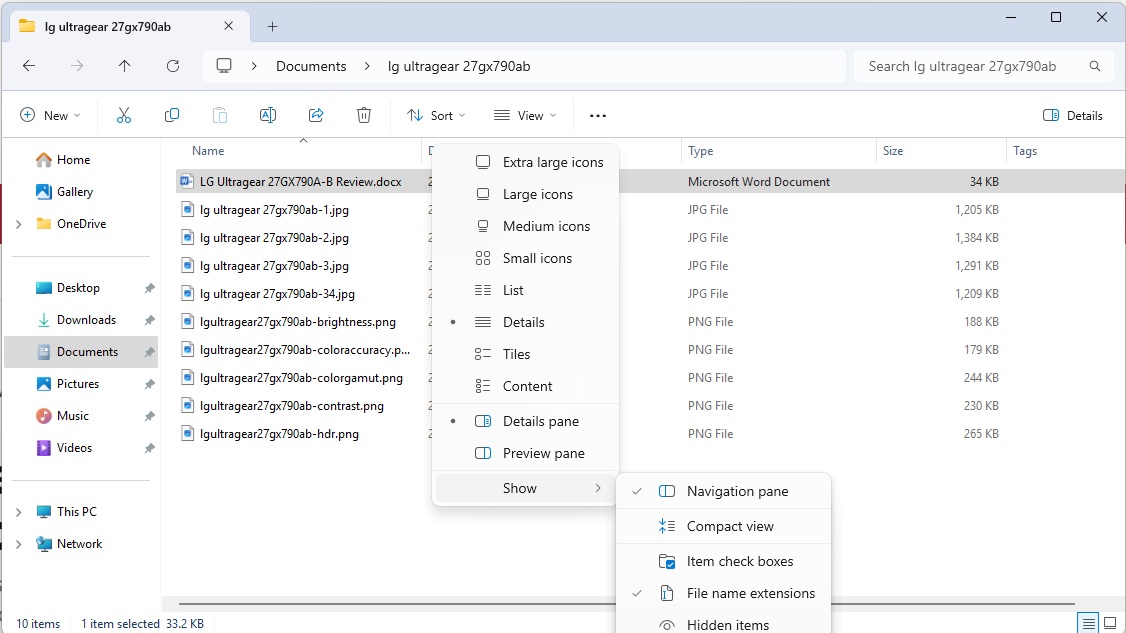 File name extensions
File name extensions
Advanced Registry Tools
While the built-in Registry Editor suffices for basic tasks, several third-party tools offer enhanced functionality:
- Regcool: Provides advanced features like quick search, bookmarks, comments, registry comparison, and backup creation.
- Regshot: Creates registry snapshots for comparison, highlighting changes made between snapshots.
- Registry Finder: Offers lightning-fast search, tabbed results, and detailed bookmarking with descriptions, categories, and tags.
- Reg Ownership Ex: Simplifies managing registry access permissions.
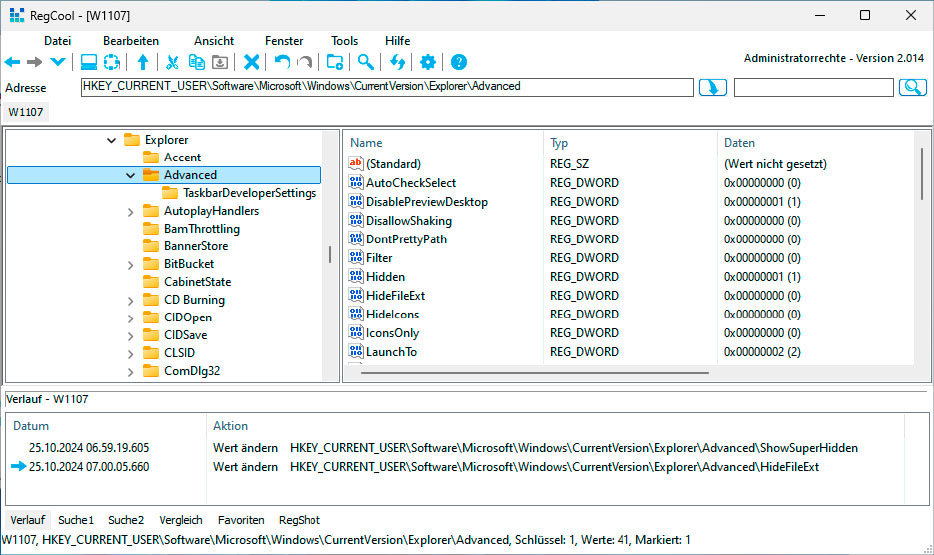 Alternativer Registry-Editor: Regcool bietet eine schnelle Suche und zahlreiche Komfortfunktionen beim Umgang mit der Registry, beispielsweise Lesezeichen und Registry-Vergleich.
Alternativer Registry-Editor: Regcool bietet eine schnelle Suche und zahlreiche Komfortfunktionen beim Umgang mit der Registry, beispielsweise Lesezeichen und Registry-Vergleich.
Limitations and Protections
Microsoft has implemented measures to restrict registry modifications, particularly for settings related to security and default applications. The User Choice Protection Driver (UCPD) prevents unauthorized changes to settings like the default browser, safeguarding against malware manipulation. However, workarounds exist, illustrating the ongoing dynamic between user control and system security.
Privacy and Security Settings
Windows transmits diagnostic data (telemetry) to Microsoft. While this aids in error detection and system improvement, it raises privacy concerns. Tools like O&O Shutup10 and W10Privacy offer granular control over these settings, allowing users to customize data collection according to their preferences. These tools simplify managing complex privacy-related registry entries, providing clear descriptions and recommendations.
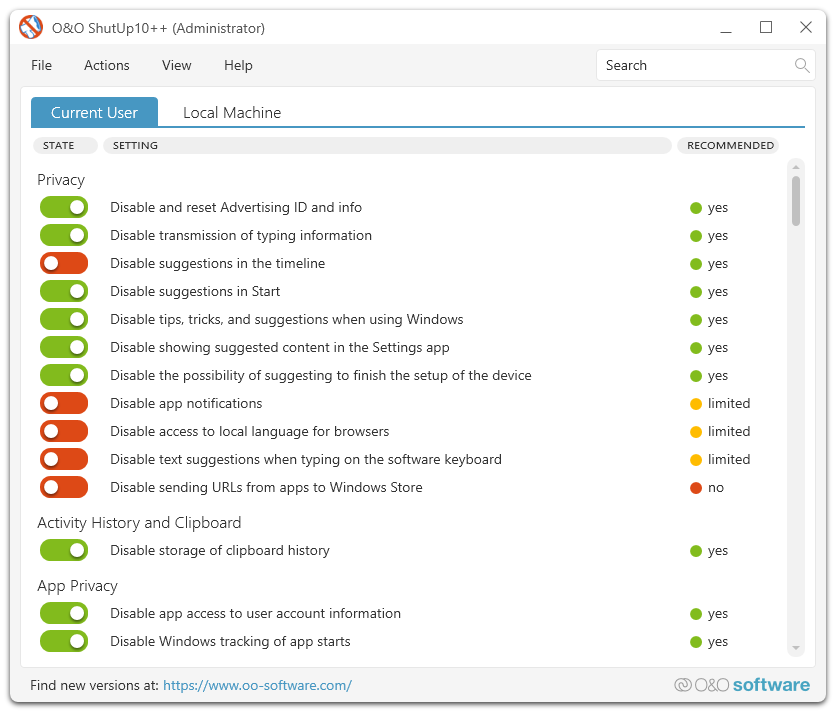 O&O Shutup
O&O Shutup