The digital age has made computer security paramount. While smartphones are ubiquitous, computers remain vulnerable due to their extensive capabilities. This guide provides practical steps to safeguard your Windows PC from data loss, malware, and unauthorized access.
 Protecting Your Windows PC
Protecting Your Windows PC
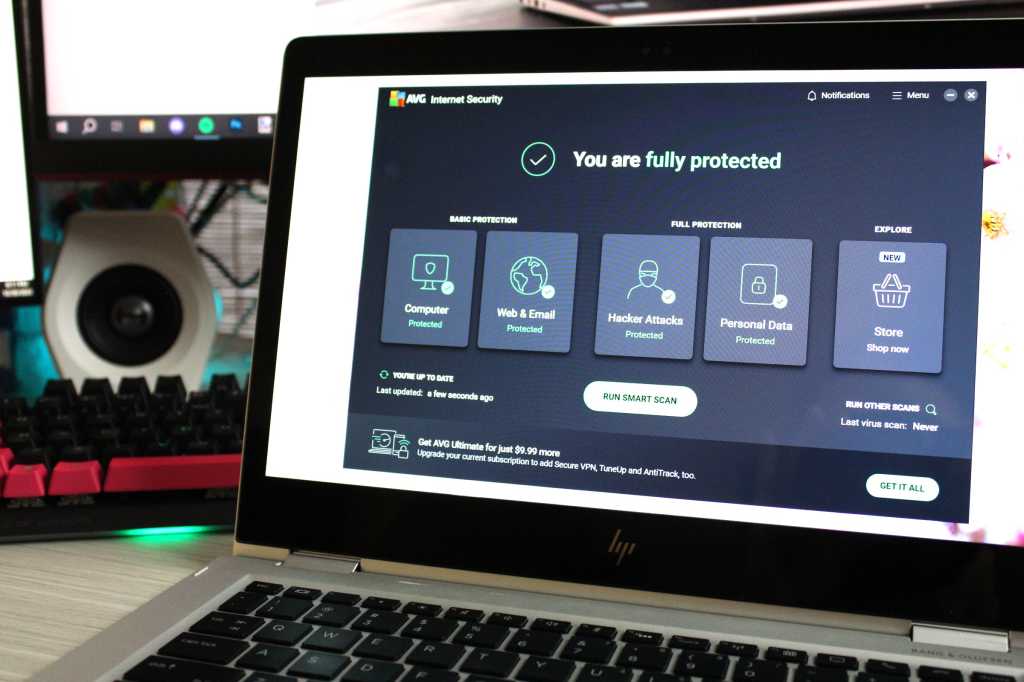
Essential Antivirus Protection
While Windows Defender offers decent protection, a dedicated antivirus program remains crucial. Modern malware, particularly ransomware, can cause significant damage, encrypting your data and demanding hefty ransoms. Top-tier antivirus software often includes advanced features like real-time monitoring and behavioral analysis to detect and neutralize threats, including zero-day exploits.
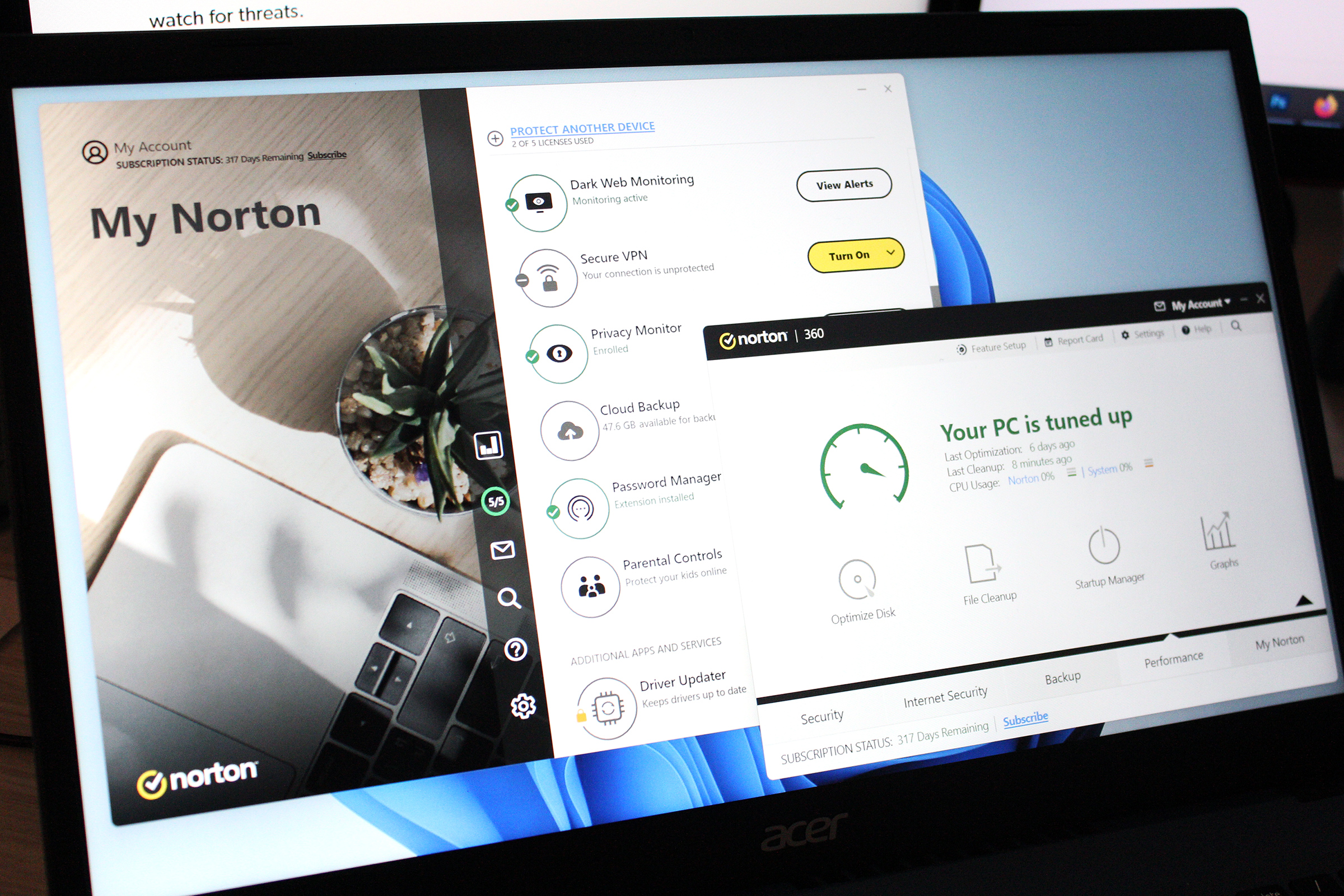
Recommended Antivirus: Norton 360 Deluxe
 Norton 360 Deluxe
Norton 360 Deluxe
Read our review
- Price When Reviewed: $49.99 for the first year
- Best Prices Today: $19.99 at PCWorld Software Store | $49.99 at Norton
The Importance of Software Updates
Maintaining updated software is as critical as antivirus protection. Regular updates patch security vulnerabilities, preventing malware from exploiting known weaknesses. Prioritize updating Windows, web browsers (Chrome, Firefox, Brave, etc.), and communication applications like email clients (Outlook, Thunderbird) and chat platforms (Slack, Discord). Software that handles external files, such as Acrobat and Word, also requires regular updates.
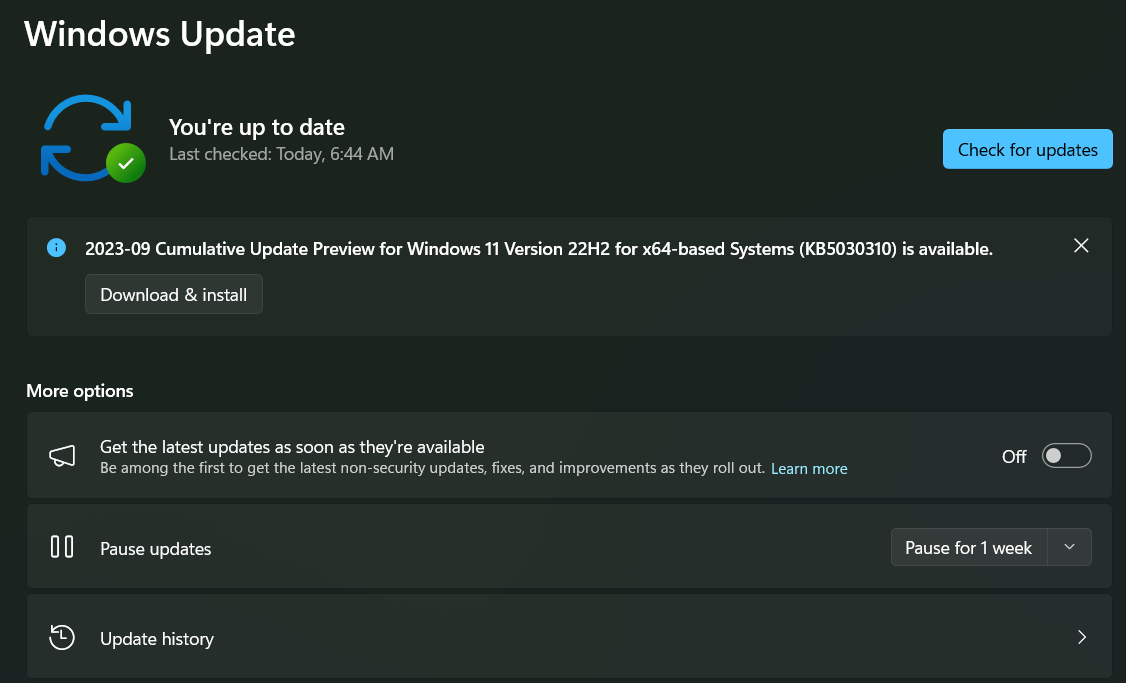 Windows Update
Windows Update
Secure Legacy Software with Virtual Machines
For older or specific software versions that can’t be updated, consider using a virtual machine (e.g., VMware Workstation). This isolates the application, mitigating risks associated with potential vulnerabilities. This approach is particularly suitable for infrequently used applications and those without demanding graphical requirements.
 Running Software in a Virtual Machine
Running Software in a Virtual Machine
Common Malware Infection Vectors
Even with robust security measures, understanding common malware delivery methods is vital. Be cautious of email attachments, social media links, automatic downloads, pirated software, and even compromised legitimate programs. Be wary of fake virus alerts prompting you to download “antivirus” software; these are often deceptive tactics to install malware.
Admin Privileges: Exercise Caution
Many malware strains require administrative privileges to infect your system. Exercise caution when granting applications these permissions. The standard Windows prompt “Do you want this app to make changes to your device?” should not be dismissed lightly. Scrutinize the requesting application before granting access.
 Windows Security Prompt
Windows Security Prompt
Data Backup: An Essential Safeguard
Regular backups are paramount to protecting your valuable data against ransomware, hardware failures, theft, and other unforeseen events. The 3-2-1 backup strategy is recommended: three copies of your data, on two different media types, with one copy stored offsite.
Recommended Online Backup: iDrive Online Cloud Backup
 iDrive Online Cloud Backup
iDrive Online Cloud Backup
Read our review
- Price When Reviewed: $79.50
- Best Prices Today: $79.50 at iDrive
 NAS Drive for Backups
NAS Drive for Backups
- Further reading: Best Windows backup software
- Further reading: Best cloud backup services
Encrypting Sensitive Data
Encryption protects your data from unauthorized access. While mobile operating systems often have built-in encryption, Windows users need to take proactive steps. BitLocker, available with Windows Pro licenses, provides full-disk encryption. Veracrypt is a free alternative offering both full-disk and container encryption.
- Further reading: How to encrypt files in Windows
Conclusion
Protecting your Windows computer requires a multi-layered approach encompassing antivirus software, regular updates, safe browsing habits, and robust backup and encryption strategies. By implementing these measures, you can significantly enhance your digital security and protect your valuable data.