The convenience of a smart home comes at a price: increased technical complexities, particularly concerning data security. This guide explores the potential risks and offers practical advice for safeguarding your connected home.
Choosing the Right Smart Home System
The smart home market offers two primary options: professionally installed systems and retrofittable components from various manufacturers. While the latter offers DIY convenience, it often introduces a range of security concerns overlooked by many users. This guide will help you mitigate those risks before and after purchase.
The Cloud Conundrum: Minimize Reliance
Many manufacturers require internet connectivity for remote device control. For instance, Xiaomi’s smart lamps and fans require a smartphone app, mandating cloud integration and use of voice assistants like Alexa or Google Home. This opens the door to potential vulnerabilities, as evidenced by unsecured webcams accessible through search engines like Shodan. Before purchasing, check reviews for mandatory cloud integration and prioritize local control solutions whenever possible. Alternatives like Raspbee or Conbee bridges offer cloud-free control for compatible devices. Consider the necessity of each feature: convenient temperature control doesn’t always require smartphone-based geofencing, which relies on internet connectivity.
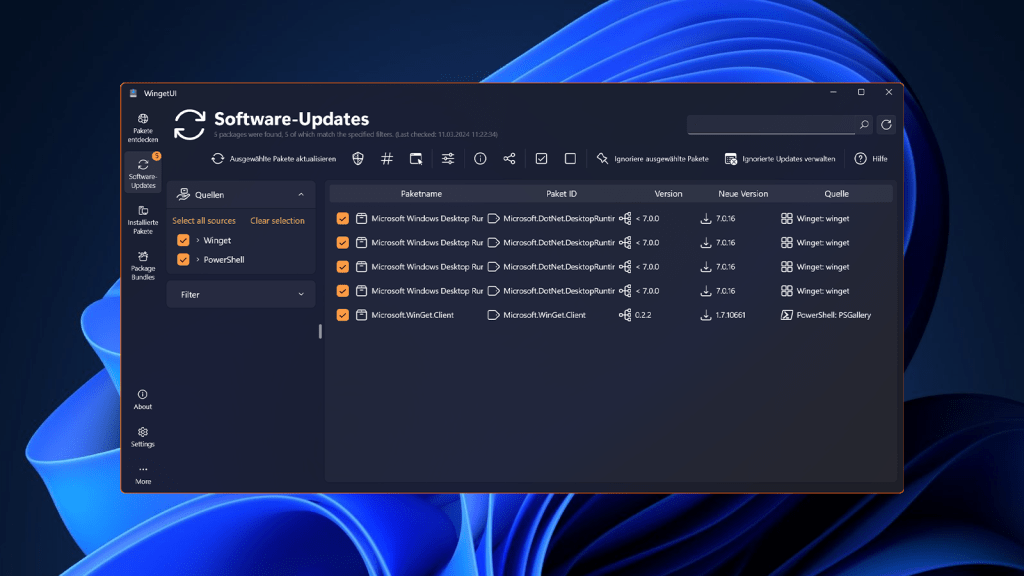
 Open VAS (also included with Kali Linux) analyzes the local network and all devices for vulnerabilities and configuration errors.
Open VAS (also included with Kali Linux) analyzes the local network and all devices for vulnerabilities and configuration errors.
Security risks extend beyond your network. Compromised devices can become part of botnets, rendering them unusable and leading to legal complications.
Wi-Fi Connectivity: A Double-Edged Sword
Wi-Fi-connected devices offer simple setup using an app to store network credentials. However, this exposes them to the same vulnerabilities as your wireless network. Manufacturers often highlight convenience while obscuring the Wi-Fi standards used. Devices using alternative standards like Zigbee are generally more secure than flooding your Wi-Fi network with numerous IoT devices. If Wi-Fi is unavoidable, isolate smart home devices on a separate guest network, a feature offered by routers like Fritzbox.
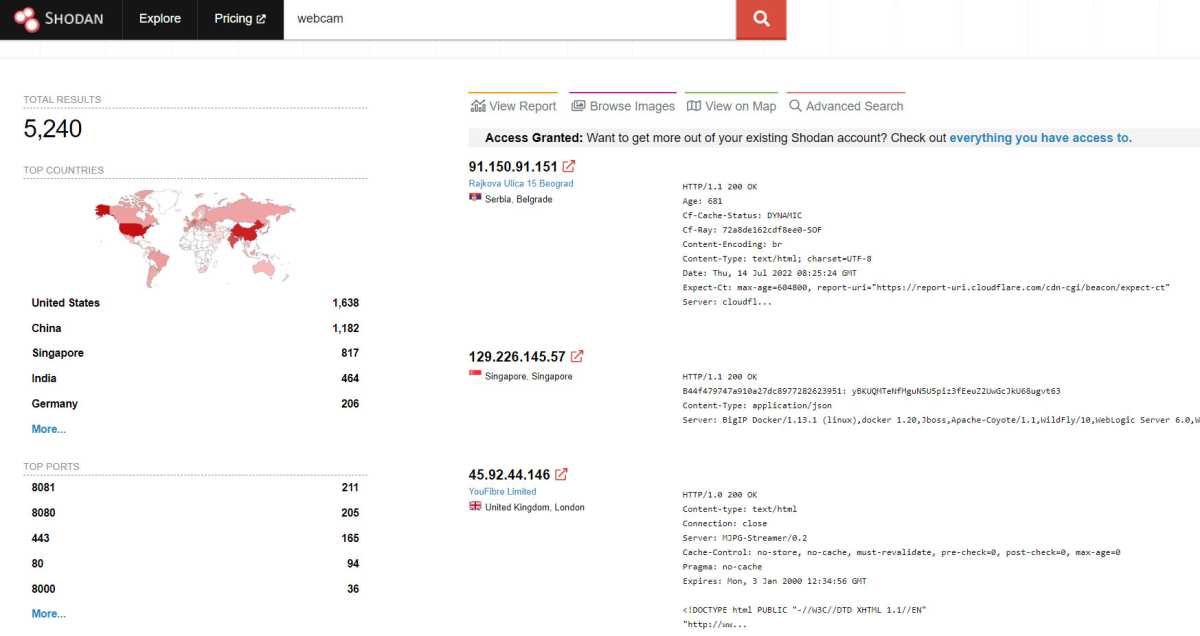 The Shodan search engine produces astonishing results. Inadequately secured webcams often allow people to look into other people’s homes.
The Shodan search engine produces astonishing results. Inadequately secured webcams often allow people to look into other people’s homes.
Router Security: Your First Line of Defense
Prioritize securing your router, a common source of vulnerabilities. Forgotten open ports and exploitable protocols like Universal Plug and Play (UPnP) pose significant risks. UPnP simplifies device discovery and connection within a network. However, if a device with vulnerable firmware can independently configure port forwarding, it creates an entry point for external access and botnet recruitment. Adopt a blacklist approach: disable all unnecessary external connections to devices within your network.
Centralized Control: Balancing Convenience and Security
Multiple device-specific apps quickly become unwieldy. While platforms like Apple HomeKit, Google Home, and Alexa offer centralized control, they potentially introduce additional vulnerabilities. Tech-savvy users can opt for open-source platforms like OpenHAB, Domoticz, or ioBroker for greater control, transparency, and cross-device automation.
Vulnerability Scanning: Proactive Security
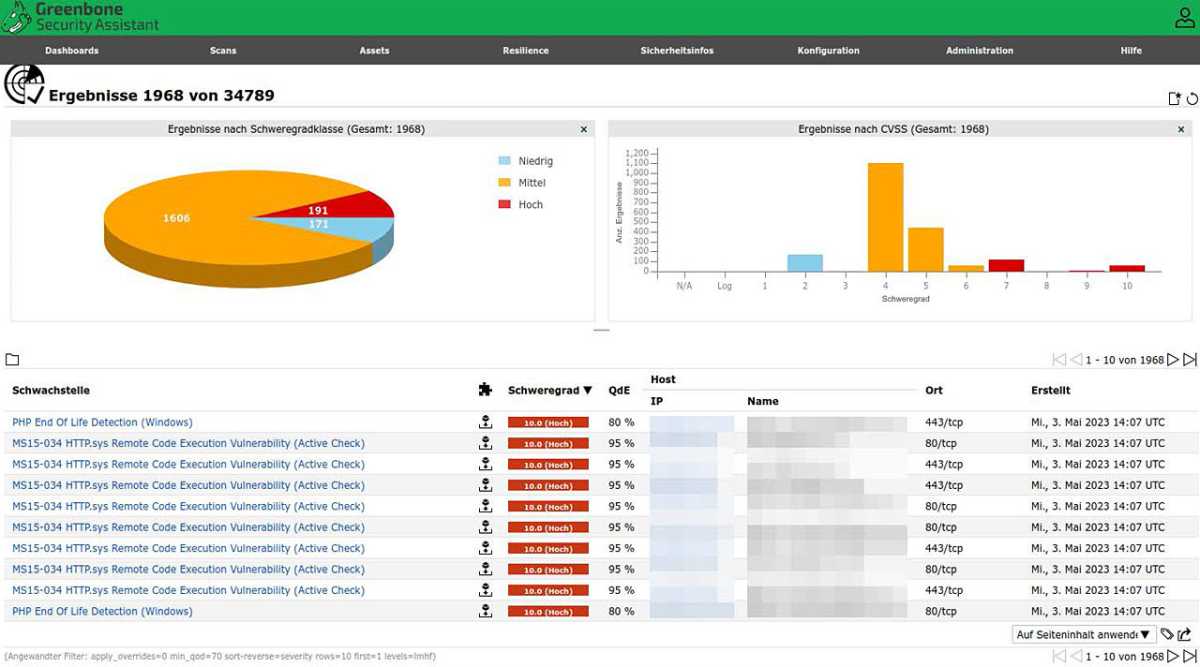
 Tools such as Open VAS usually provide unique CVE numbers for vulnerabilities found, which you can then use to search for patches and possible solutions.
Tools such as Open VAS usually provide unique CVE numbers for vulnerabilities found, which you can then use to search for patches and possible solutions.
Tools like Open VAS (Open Vulnerability Assessment System), available commercially through Greenbone, scan your network for vulnerabilities. Install it via Docker, source code, or use Kali Linux, which includes Open VAS. Scanning generates a detailed report with CVE (Common Vulnerabilities and Exposures) numbers, enabling you to research potential threats and find patches.
Detecting active attacks requires specialized tools like Suricata (available on Kali Linux) to analyze network traffic. However, interpreting the results requires networking expertise and protocol knowledge, which goes beyond the scope of this introductory guide.
Conclusion: A Secure Smart Home Requires Vigilance
Securing your smart home is an ongoing process. By carefully selecting devices, minimizing cloud reliance, securing your router, and proactively scanning for vulnerabilities, you can significantly reduce the risks associated with connected devices and enjoy the benefits of a truly smart and secure home.