Many Windows 10 and 11 Home users are unaware of the built-in encryption tool, often activated by default. While Microsoft emphasizes BitLocker for Pro versions, Home editions offer “Device Encryption,” providing similar data protection. This guide explains how to utilize and understand this crucial security feature.
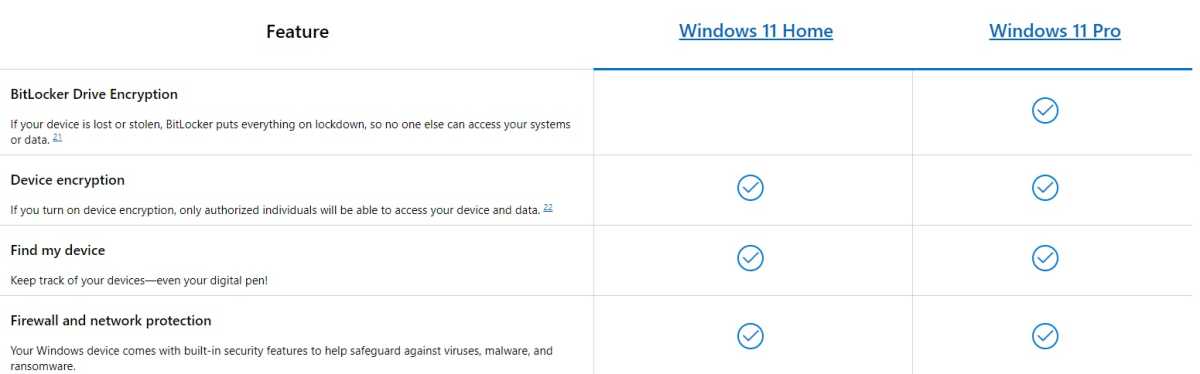 Windows BitLockerAlthough Microsoft promotes BitLocker for Windows Pro, Home editions offer “Device Encryption” for robust data security.
Windows BitLockerAlthough Microsoft promotes BitLocker for Windows Pro, Home editions offer “Device Encryption” for robust data security.
Why is encryption so vital? It prevents unauthorized access even if your hard drive is removed. This is especially important for laptops, which are vulnerable to theft or loss. Unlike simply logging in, encryption safeguards your data at a deeper level.
System Requirements for Device Encryption
Four prerequisites must be met for Device Encryption:
-
UEFI: Your PC needs a modern UEFI (Unified Extensible Firmware Interface), replacing the older BIOS. This is standard on most modern computers.
-
TPM Chip: A Trusted Platform Module (TPM) chip is essential. This hardware component enhances security.
-
Modern Standby: Your device must support Modern Standby (S0) power-saving mode. Check this by opening Command Prompt as administrator and entering
powercfg /a. Look for “Standby (S0 low power state) … available on this system.” If not supported, consult your manufacturer or UEFI settings. -
Secure Boot: This option must be enabled in your UEFI settings. Accessing UEFI settings varies by manufacturer, so you might need to consult your device’s documentation.
For a final compatibility check, open System Information by typing msinfo in the search bar and running it as administrator. Look for “Support for device encryption.” If the requirements are not met, hover over the entry to see the reason. A common issue is “PCR7 binding,” often related to the prerequisites above.
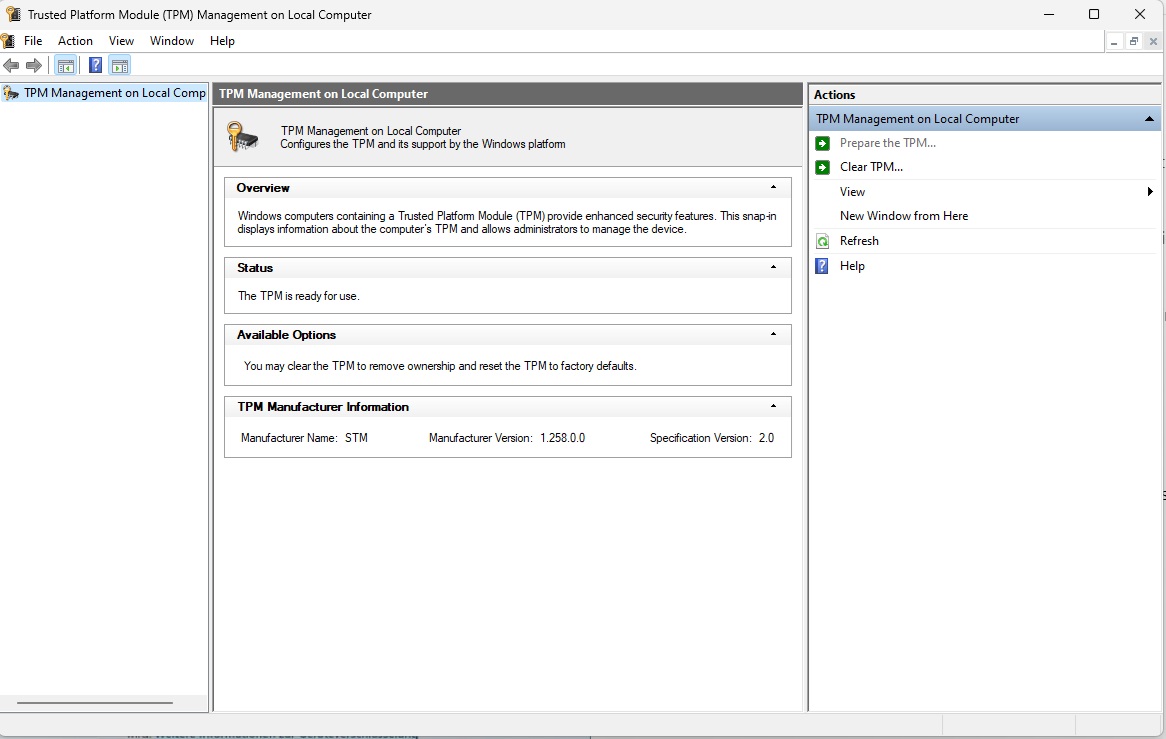 TPM WindowsVerify that your TPM is active and version 2.0 is enabled.
TPM WindowsVerify that your TPM is active and version 2.0 is enabled.
To check your TPM status, type tpm.msc in the search bar. Ensure the status is “The TPM is ready for use” and the specification version is “2.0”. If not, enable TPM in your UEFI settings and run the TPM setup wizard (tpm.msc) afterwards by clicking “Prepare TPM.” Also ensure Secure Boot is enabled in your UEFI.
Enabling Device Encryption
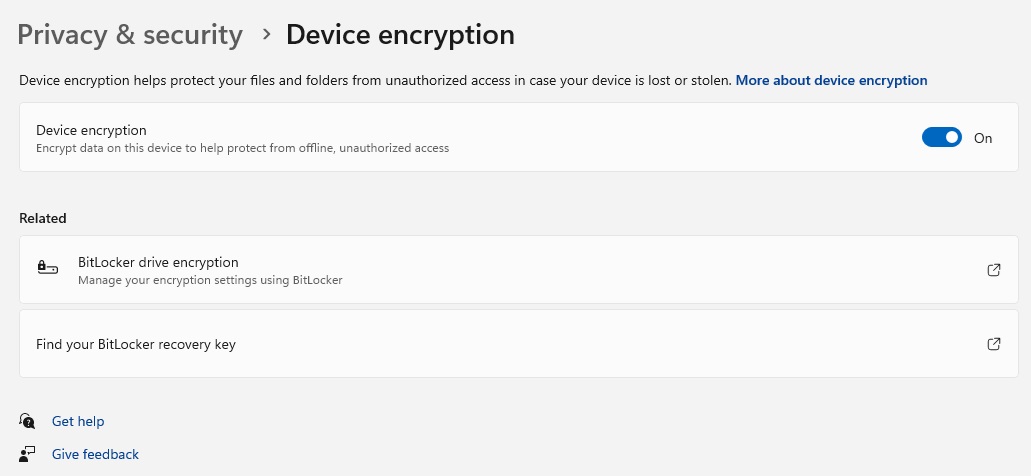 Windows device encryptionEnable Device Encryption in Windows Settings.
Windows device encryptionEnable Device Encryption in Windows Settings.
After confirming the prerequisites, navigate to “Privacy & security” (Windows 11) or “Update & security” (Windows 10) in the Settings app. Locate “Device encryption” and toggle it on. Crucially, you must be logged in with a Microsoft account for this to function. Local accounts are not supported.
While BitLocker in Pro editions offers extensive customization, Device Encryption in Home versions is simpler. It provides robust protection with 128-bit encryption, effectively securing your data. An open lock icon beside your drives in File Explorer indicates active encryption.
For more detailed information, use the manage-bde -status c: command in an elevated Command Prompt. Focus on “Conversion Status” and “Protection Status.” “Unlocked” lock status is normal while you are logged in. Note that many manage-bde parameters are BitLocker-specific.
Troubleshooting Device Encryption
Setup issues are common, usually stemming from incorrect UEFI settings or unmet system requirements. Online research can often resolve these. If hardware incompatibility is the problem, consider third-party encryption software like Veracrypt (discussed below).
Unexpected issues can arise, such as needing a recovery key after a UEFI update. Remain calm, investigate the cause, and seek solutions.
Recovery Key and Emergency Access
While setup might seem complex, Device Encryption operates seamlessly in the background. It automatically unlocks your drive upon login and encrypts it upon logout or shutdown. A strong Microsoft account password and two-factor authentication (2FA) are highly recommended. Windows Hello (PIN, fingerprint, or facial recognition) offers convenient login options.
To prepare for emergencies like hardware failure, Windows generates a 48-digit recovery key. Access this key at https://account.microsoft.com/devices/recoverykey. Save it securely in a password manager or print a copy. Multiple partitions (OSV for the system drive, FDV for data drives) may have separate keys.
Veracrypt: A Flexible Alternative
 VeracryptVeracrypt offers flexible encryption options.
VeracryptVeracrypt offers flexible encryption options.
Veracrypt offers more flexibility than Device Encryption, encrypting individual partitions, folders, files, and removable drives. This is particularly useful for Windows Home users. It also has less stringent system requirements.
Before installing Veracrypt, ensure Device Encryption is disabled (manage-bde -status c:) and back up your data.
Master these Windows features to supercharge your efficiency.