Mac users face a new malware threat known as Cthulhu Stealer, designed to pilfer sensitive information like passwords, cryptocurrency wallets, and more, according to a report by Cado Security. This malware masquerades as legitimate software to trick users into providing their login credentials.
How Cthulhu Stealer Works
Cthulhu Stealer arrives disguised as an Apple disk image (.dmg) file containing two binaries, tailored to different system architectures. Written in Golang, the malware mimics authentic applications. Upon mounting the .dmg, users are prompted to open the software. Once launched, it uses osascript, the macOS command-line tool for AppleScript and JavaScript execution, to request the user’s password.
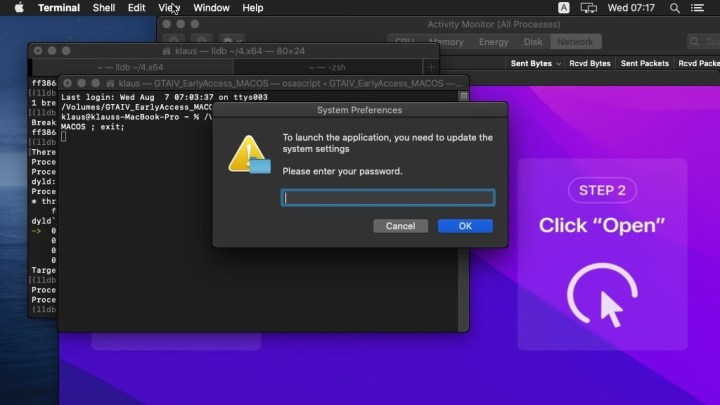 Mac password prompt.
Mac password prompt.
Following this initial prompt, a second request appears for the user’s MetaMask password. This tactic is also employed by other malware like Cuckoo, Atomic Stealer, and Banshee Stealer. Distinctively, Cthulhu Stealer aims to collect system data and extract iCloud Keychain passwords using a tool called Chainbreaker.
Cthulhu Stealer’s Disguises and Data Exfiltration
This new threat can impersonate various software applications, including AdobeGenP, CleanMyMac, and even Grand Theft Auto IV, exploiting the familiar DMG format to deceive users. The allure of using cracked software like AdobeGenP without a license or subscription makes this a particularly insidious tactic.
After collecting data, including Telegram account details and web browser cookies, Cthulhu Stealer compresses the stolen information into a ZIP archive and transmits it to a command-and-control (C2) server controlled by the attackers. The malware shares striking similarities with Atomic Stealer, exhibiting identical spelling errors and functional overlaps, suggesting code reuse and modification by the developer.
Protecting Yourself from Cthulhu Stealer
Users can take several precautions to mitigate the risk:
- Download software exclusively from trusted sources: Avoid downloading applications from unofficial websites or untrusted sources.
- Keep your macOS updated: Ensure your system is running the latest version of macOS to benefit from the latest security patches.
- Consider antivirus software: Installing reputable antivirus software for Mac can provide an additional layer of protection.
Apple’s Response to Rising Mac Malware
Recognizing the increasing prevalence of Mac malware, Apple has implemented significant security enhancements. With macOS Sequoia, users will no longer be able to bypass Gatekeeper protections by Control-clicking on unsigned or un-notarized software. Instead, users must navigate to System Settings > Privacy & Security to review the security information before executing the application.
Conclusion
Cthulhu Stealer represents a serious threat to Mac users, highlighting the importance of vigilance and proactive security measures. By staying informed about emerging threats and adopting safe computing practices, users can significantly reduce their risk of falling victim to this and other malware attacks. Staying updated with macOS security features and using trusted software sources are crucial steps in maintaining a secure computing environment.